Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 23 dezembro 2024

Automated Use-After-Free Detection and Exploit Mitigation: How Far
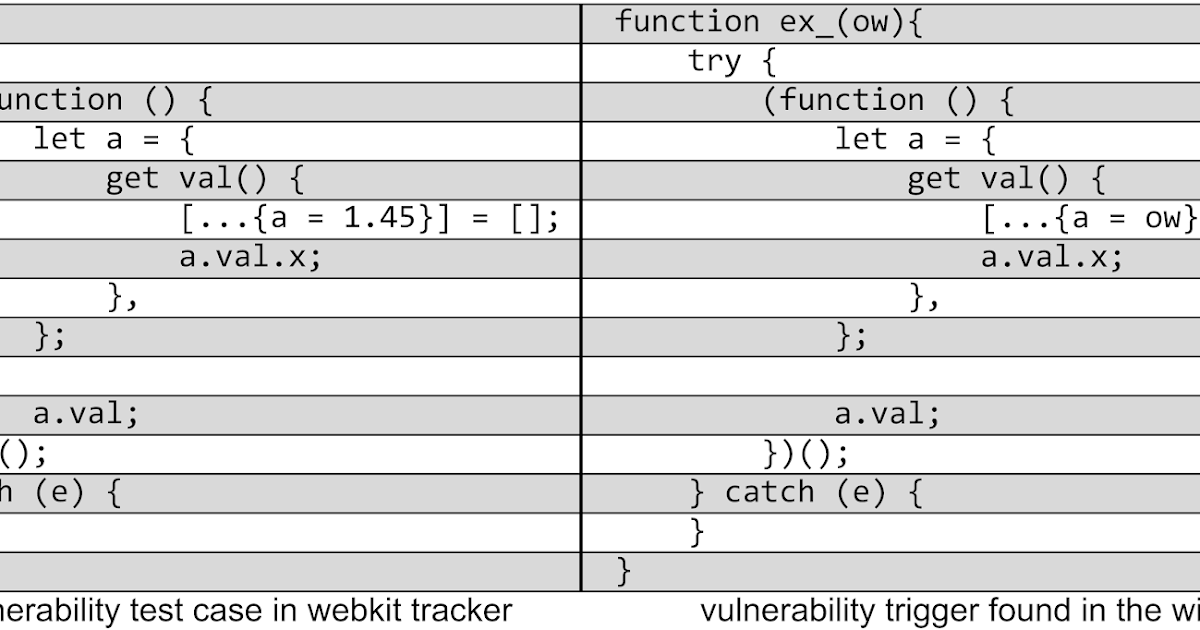
Project Zero: JSC Exploits
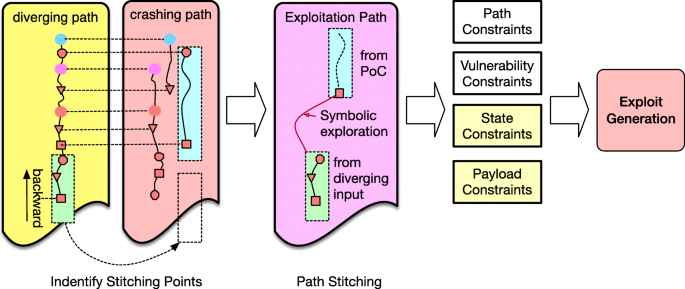
From proof-of-concept to exploitable, Cybersecurity
First Binder Exploit Linked to SideWinder APT Group

Exploiting a Use-After-Free (UAF) Vulnerability - Unsubscriptions

Exploit Database SearchSploit Manual

Heap Exploit Development

PDF) Authenticator Rebinding Attack of the UAF Protocol on Mobile
SemFuzz: Semantics-based Automatic Generation of Proof-of-Concept

The components of Dr. Memory. The original application's code is
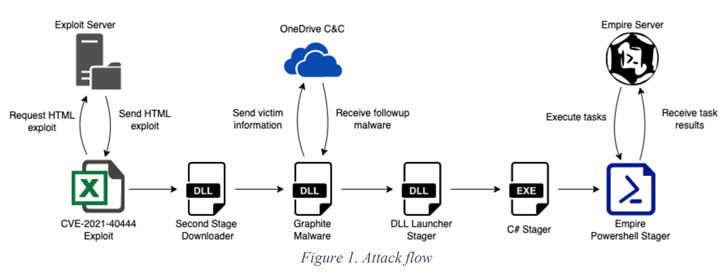
Hackers Exploited MSHTML Flaw to Spy on Government and Defen
USP1-trapping lesions as a source of DNA replication stress and
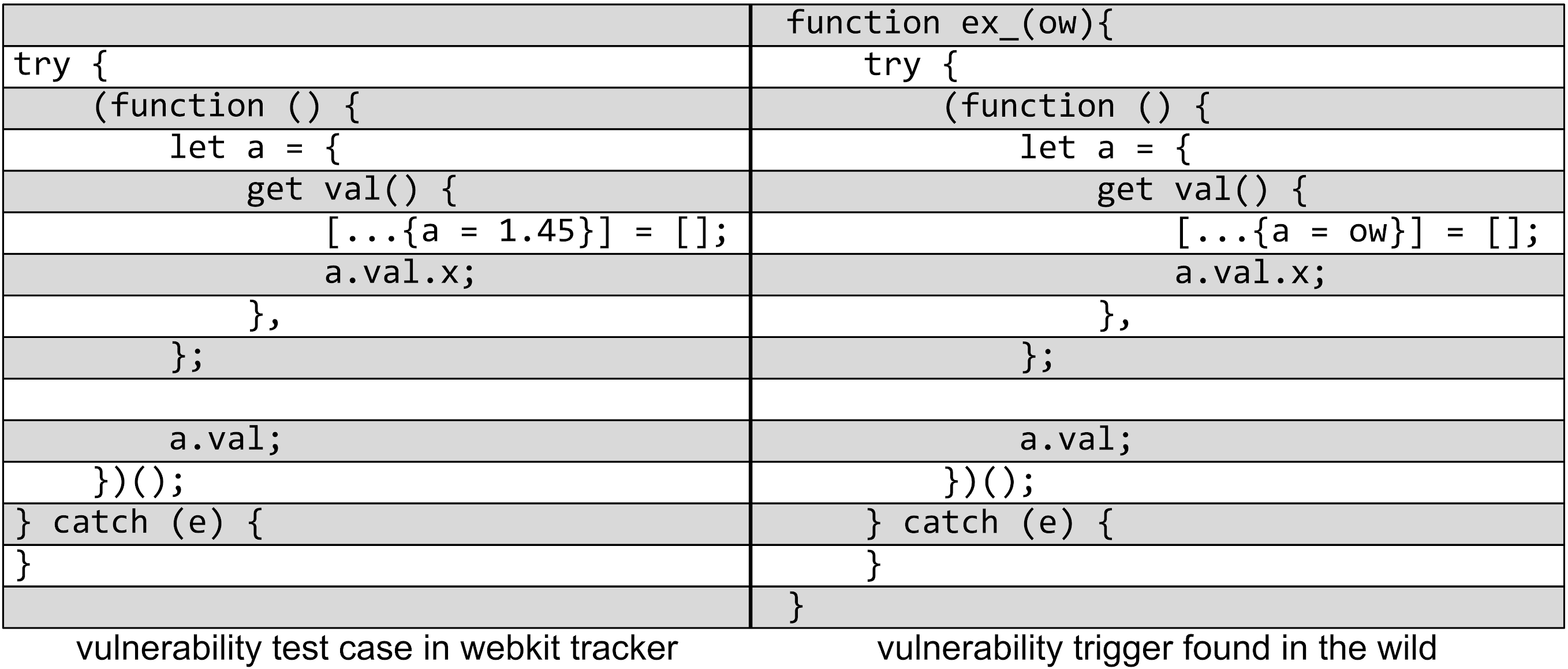
Project Zero: JSC Exploits
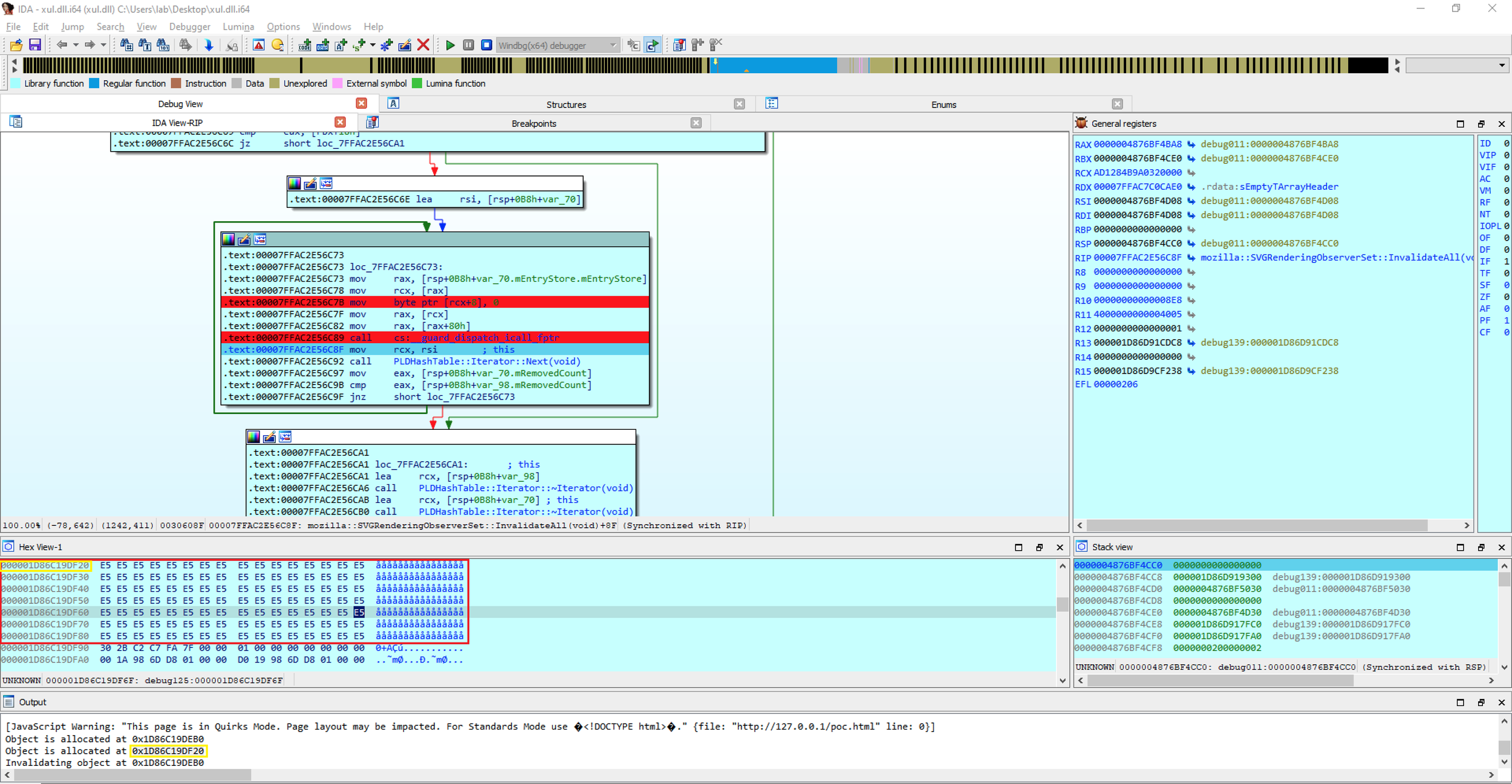
CVE-2022-26381: Gone by others! Triggering a UAF in Firefox
Complete UAF exploit - UD Capture
Recomendado para você
-
 KING LEGACY – ScriptPastebin23 dezembro 2024
KING LEGACY – ScriptPastebin23 dezembro 2024 -
 Roblox King Legacy Script Pastebin Hacks – December 202323 dezembro 2024
Roblox King Legacy Script Pastebin Hacks – December 202323 dezembro 2024 -
 KING LEGACY – ScriptPastebin23 dezembro 2024
KING LEGACY – ScriptPastebin23 dezembro 2024 -
 Partnerships Archives - FSULIB23 dezembro 2024
Partnerships Archives - FSULIB23 dezembro 2024 -
 Loras College Legacy Symposium 2015 Abstracts by Loras College - Issuu23 dezembro 2024
Loras College Legacy Symposium 2015 Abstracts by Loras College - Issuu23 dezembro 2024 -
 Elemental Dungeons Script (December 2023) - Droid Local23 dezembro 2024
Elemental Dungeons Script (December 2023) - Droid Local23 dezembro 2024 -
 Course Descriptions - University Catalogs - University of Minnesota23 dezembro 2024
Course Descriptions - University Catalogs - University of Minnesota23 dezembro 2024 -
 Course DesCriptions - University Catalogs - University of Minnesota23 dezembro 2024
Course DesCriptions - University Catalogs - University of Minnesota23 dezembro 2024 -
 Patterson Accepts Presidency at Chadron State College23 dezembro 2024
Patterson Accepts Presidency at Chadron State College23 dezembro 2024 -
 Grand Theft Auto V - Xbox 360 : Take 2 Interactive: Video Games23 dezembro 2024
Grand Theft Auto V - Xbox 360 : Take 2 Interactive: Video Games23 dezembro 2024
você pode gostar
-
 Here's a trailer to remind you to pay to play Fortnite now even though it will be free next year23 dezembro 2024
Here's a trailer to remind you to pay to play Fortnite now even though it will be free next year23 dezembro 2024 -
 TAS mantém exclusão das equipas russas das provas da UEFA de 2022/2323 dezembro 2024
TAS mantém exclusão das equipas russas das provas da UEFA de 2022/2323 dezembro 2024 -
 Watch Game Shakers23 dezembro 2024
Watch Game Shakers23 dezembro 2024 -
 Walleva Replacement Lenses for Oakley Penny Sunglasses - Multiple23 dezembro 2024
Walleva Replacement Lenses for Oakley Penny Sunglasses - Multiple23 dezembro 2024 -
 Returnal' Steam updates suggest Housemarque's shooter is coming to PC23 dezembro 2024
Returnal' Steam updates suggest Housemarque's shooter is coming to PC23 dezembro 2024 -
 Comco Ikarus C42, Light Sport Aircraft in the U.S., Advanced Ultralight in Canada.23 dezembro 2024
Comco Ikarus C42, Light Sport Aircraft in the U.S., Advanced Ultralight in Canada.23 dezembro 2024 -
 Kimetsu no Yaiba - Moztudo - Download23 dezembro 2024
Kimetsu no Yaiba - Moztudo - Download23 dezembro 2024 -
 Blue Lock Filmes de anime, Anime, Animes para assistir23 dezembro 2024
Blue Lock Filmes de anime, Anime, Animes para assistir23 dezembro 2024 -
 Golden Age of Narnia, The Chronicles of Narnia Wiki23 dezembro 2024
Golden Age of Narnia, The Chronicles of Narnia Wiki23 dezembro 2024 -
 Copa do Mundo 2022: Quem vai ganhar o jogo Brasil x Coréia? FIFA23 dezembro 2024
Copa do Mundo 2022: Quem vai ganhar o jogo Brasil x Coréia? FIFA23 dezembro 2024