Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Last updated 22 dezembro 2024

Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools

Penetration Testing Attacks — Credential Stuffing, EC Council, by EC-Council Group
How to Bypass Cloudflare in 2023: The 8 Best Methods - ZenRows

The credential stuffing bots are back, and still not playing fair
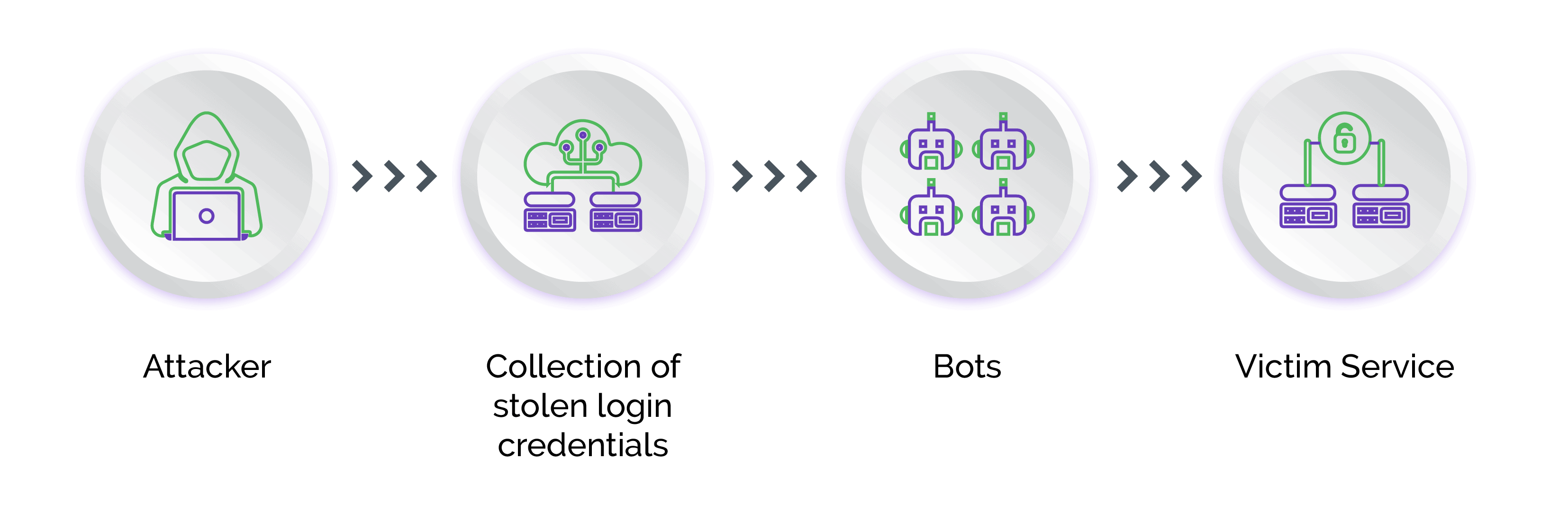
What Is Credential Stuffing?
How to Bypass Cloudflare Bot Protection? Web Scraping Service in 2023
CheatSheetSeries/cheatsheets/Credential_Stuffing_Prevention_Cheat_Sheet.md at master · OWASP/CheatSheetSeries · GitHub
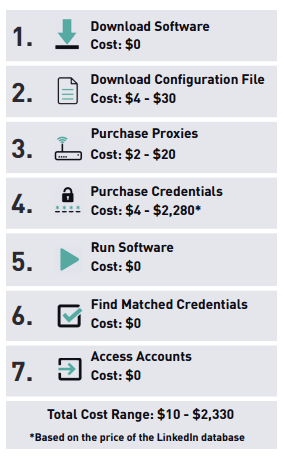
Password Breaches Fueling Booming Credential Stuffing Business

Application Level Hijacking Using Proxy Hacking - GeeksforGeeks
Recomendado para você
-
GitHub - 1kd/Discord-IP-Grabber: Grabs a targets IP address and22 dezembro 2024
-
Omegle IP locator22 dezembro 2024
-
IP Address Finder22 dezembro 2024
-
 DW IP Finder22 dezembro 2024
DW IP Finder22 dezembro 2024 -
 IP Address Tracker - IP Tracker (Free Trial)22 dezembro 2024
IP Address Tracker - IP Tracker (Free Trial)22 dezembro 2024 -
 Track That IP-Server Locator on the App Store22 dezembro 2024
Track That IP-Server Locator on the App Store22 dezembro 2024 -
 Ip Location Plugins, Code & Scripts22 dezembro 2024
Ip Location Plugins, Code & Scripts22 dezembro 2024 -
 How to Find the IP Address of a Skype User (with Pictures)22 dezembro 2024
How to Find the IP Address of a Skype User (with Pictures)22 dezembro 2024 -
IP Logger URL Shortener - Log and Track IP addresses22 dezembro 2024
-
 80+ Best SEO Chrome Extensions - SEOSLY22 dezembro 2024
80+ Best SEO Chrome Extensions - SEOSLY22 dezembro 2024
você pode gostar
-
 BORUTO 86 87 88 sinopse – André & Desânimo tv22 dezembro 2024
BORUTO 86 87 88 sinopse – André & Desânimo tv22 dezembro 2024 -
 Ghibli Grave of the Fireflies original movie POSTER JAPAN B2 Isao Takahata F/S22 dezembro 2024
Ghibli Grave of the Fireflies original movie POSTER JAPAN B2 Isao Takahata F/S22 dezembro 2024 -
 News Farming Simulator22 dezembro 2024
News Farming Simulator22 dezembro 2024 -
 Trapt – Overloaded Lyrics22 dezembro 2024
Trapt – Overloaded Lyrics22 dezembro 2024 -
 Dragon's Dogma: Dark Arisen Gaming Graphics Performance Tweak Guide22 dezembro 2024
Dragon's Dogma: Dark Arisen Gaming Graphics Performance Tweak Guide22 dezembro 2024 -
 Abertas inscrições para cursos técnicos gratuitos do IFTM com mais22 dezembro 2024
Abertas inscrições para cursos técnicos gratuitos do IFTM com mais22 dezembro 2024 -
 PlayStation Plus Essential Games For October Leak, Include The22 dezembro 2024
PlayStation Plus Essential Games For October Leak, Include The22 dezembro 2024 -
 Dragon Ball Z Background, Desktop Wallpapers, Objfbt 1 4ai, Games Profile Picture Background Image And Wallpaper for Free Download22 dezembro 2024
Dragon Ball Z Background, Desktop Wallpapers, Objfbt 1 4ai, Games Profile Picture Background Image And Wallpaper for Free Download22 dezembro 2024 -
 Raphael Rabello on X: Mãe, tô no OneFootball! 🤩😎 Quero22 dezembro 2024
Raphael Rabello on X: Mãe, tô no OneFootball! 🤩😎 Quero22 dezembro 2024 -
 Dragon Sabo and Koala reading the news22 dezembro 2024
Dragon Sabo and Koala reading the news22 dezembro 2024