Lone-Actor Terrorism: Policy Paper 2: Attack Methodology and Logistics
Por um escritor misterioso
Last updated 31 dezembro 2024


Full article: An exploratory analysis of leakage warning behavior in lone-actor terrorists

Reshaping policies for creativity: addressing culture as a global public good

Cyber Operations during the Russo-Ukrainian War

PDF) Lone-Actor Terrorism Policy Paper 2: Attack Methodology and Logistics

China's Military and Economic Prowess in Djibouti: A Security Challenge for the Indo-Pacific > 960th Cyberspace Wing > Article Display

Algorithms and Terrorism: The Malicious Use of Artificial Intelligence for Terrorist Purposes. by UNICRI Publications - Issuu

The Dark Side: The Inside Story of How The War on Terror Turned into a War on American Ideals eBook : Mayer, Jane: Kindle Store

The IACSP's Counter-Terrorism Journal V23N2 by IACSP - Issuu

9 ~,~i - National Criminal Justice Reference Service
Recomendado para você
-
 Paper.io 2 World Conflict31 dezembro 2024
Paper.io 2 World Conflict31 dezembro 2024 -
Paper.io 2 100% Map Control Teams Assalam-U-Alaiqum, Today, I am going to play new Paper.io 2 TEAMS Mode. Please enjoy this amazing game of Paper.io 2 TEAMS Mode. I am going31 dezembro 2024
-
 World Conflict 100% - Paper.io 2 LoucosRebeldes31 dezembro 2024
World Conflict 100% - Paper.io 2 LoucosRebeldes31 dezembro 2024 -
![Paper.io 2 👩 World Conflict [GAMEPLAY] paper-io.com](https://i.ytimg.com/vi/LbS7QRuAKl8/maxresdefault.jpg) Paper.io 2 👩 World Conflict [GAMEPLAY] paper-io.com31 dezembro 2024
Paper.io 2 👩 World Conflict [GAMEPLAY] paper-io.com31 dezembro 2024 -
 World Conflict in 06:18.352 by SoggySmh - Paper.io 2 - Speedrun31 dezembro 2024
World Conflict in 06:18.352 by SoggySmh - Paper.io 2 - Speedrun31 dezembro 2024 -
how to get a big square on paper io 2|TikTok 검색31 dezembro 2024
-
 Paper.io 231 dezembro 2024
Paper.io 231 dezembro 2024 -
 우주하마 했던 땅따먹기 게임 페이퍼아이오2 (paper.io 2) : 네이버 블로그31 dezembro 2024
우주하마 했던 땅따먹기 게임 페이퍼아이오2 (paper.io 2) : 네이버 블로그31 dezembro 2024 -
 Paper.io, .io Games Wiki31 dezembro 2024
Paper.io, .io Games Wiki31 dezembro 2024 -
 Paper io 2, Nintendo Switch download software, Games31 dezembro 2024
Paper io 2, Nintendo Switch download software, Games31 dezembro 2024
você pode gostar
-
 MODERN HOUSE MINECRAFT 07 by MaxterKgb on DeviantArt31 dezembro 2024
MODERN HOUSE MINECRAFT 07 by MaxterKgb on DeviantArt31 dezembro 2024 -
 Hhgttg Magnets for Sale31 dezembro 2024
Hhgttg Magnets for Sale31 dezembro 2024 -
 Category:MAJOR 2nd Characters, Major Wiki31 dezembro 2024
Category:MAJOR 2nd Characters, Major Wiki31 dezembro 2024 -
 A big Xbox Game Studios sale has started on Steam - - Gamereactor31 dezembro 2024
A big Xbox Game Studios sale has started on Steam - - Gamereactor31 dezembro 2024 -
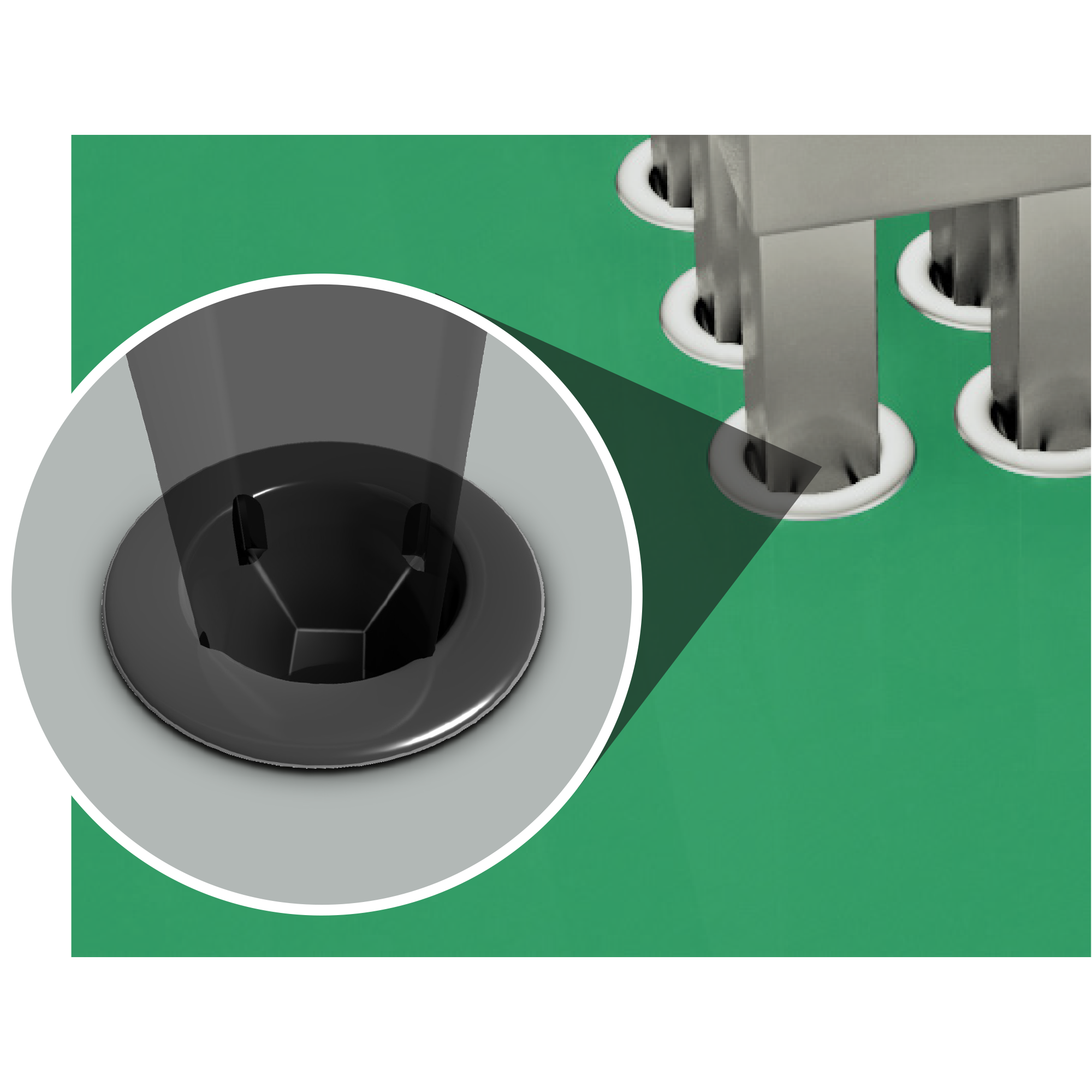 WP-BUTR REDCUBE PRESS-FIT with internal thread, two-rows31 dezembro 2024
WP-BUTR REDCUBE PRESS-FIT with internal thread, two-rows31 dezembro 2024 -
![Image - 747162], Anime / Manga](https://i.kym-cdn.com/photos/images/original/000/747/162/4b0.gif) Image - 747162], Anime / Manga31 dezembro 2024
Image - 747162], Anime / Manga31 dezembro 2024 -
 Vietnam Business Forum of Vietnam Chamber of Commerce and Industry (VCCI)-Culture & Tourism31 dezembro 2024
Vietnam Business Forum of Vietnam Chamber of Commerce and Industry (VCCI)-Culture & Tourism31 dezembro 2024 -
Disney - Pin Tico e Teco, Mansão Mal Assombrada-Original, Produto Feminino Disney Usado 7118166531 dezembro 2024
-
Design gráfico para jogos de cartas colecionáveis, Daniel Solis31 dezembro 2024
-
Servidor na bio #fy #fyp #viral #meme #memes #memebr #memesbr31 dezembro 2024




