Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace
Por um escritor misterioso
Last updated 03 janeiro 2025

In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

iOS Hacking: Advanced Pentest & Forensic Techniques

Tampering and Reverse Engineering on iOS - OWASP MASTG
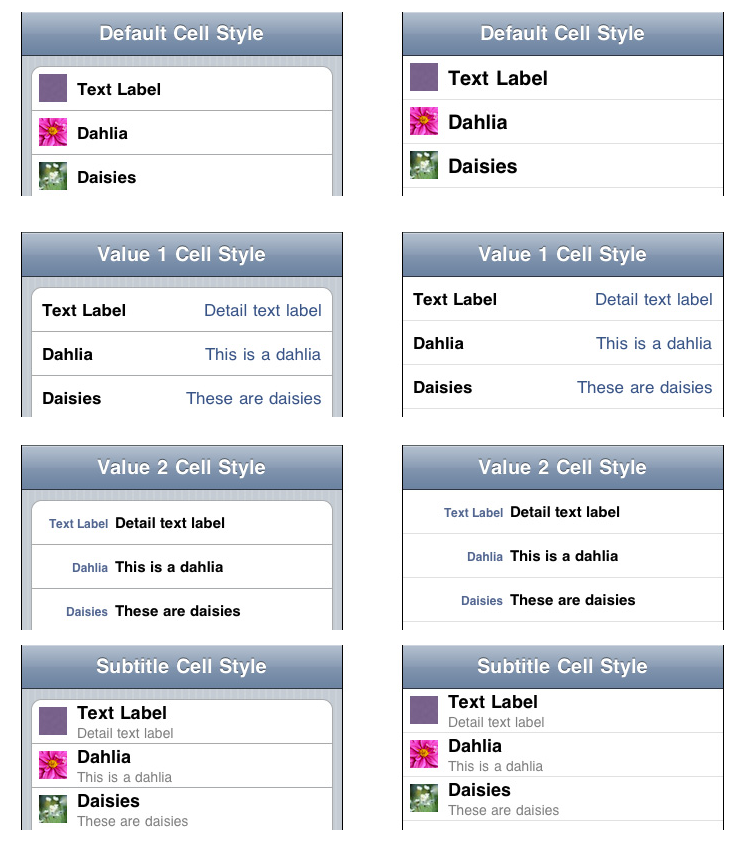
All The Quickies, Chronologically

Securing Your Fleet
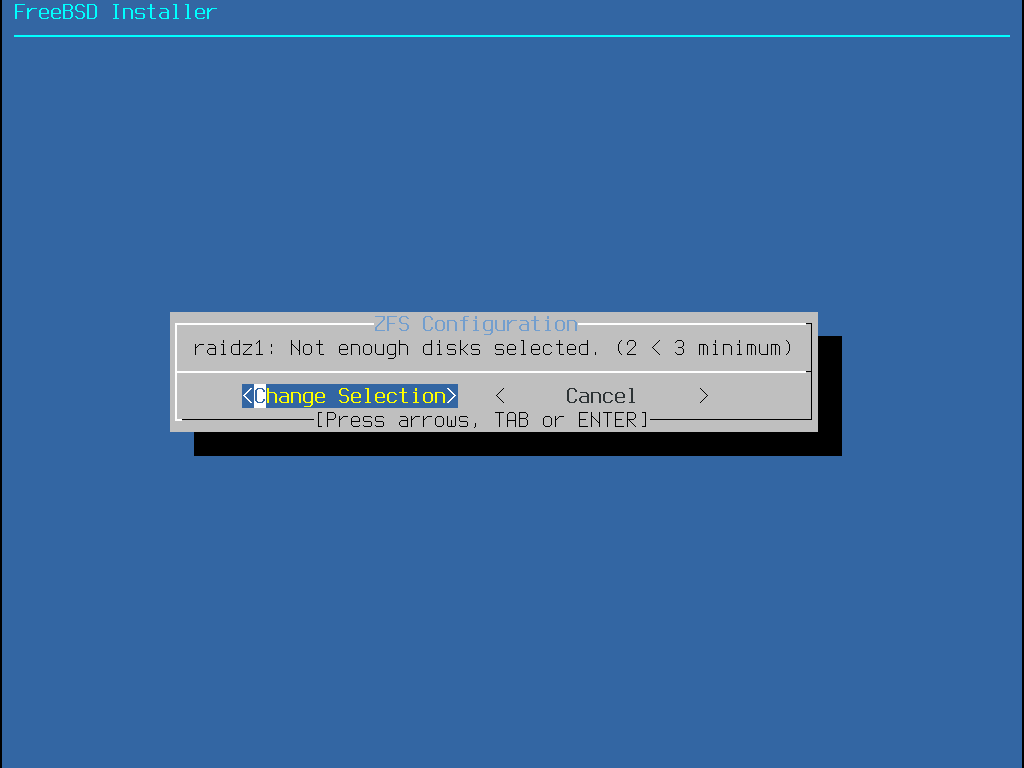
FreeBSD Handbook FreeBSD Documentation Portal
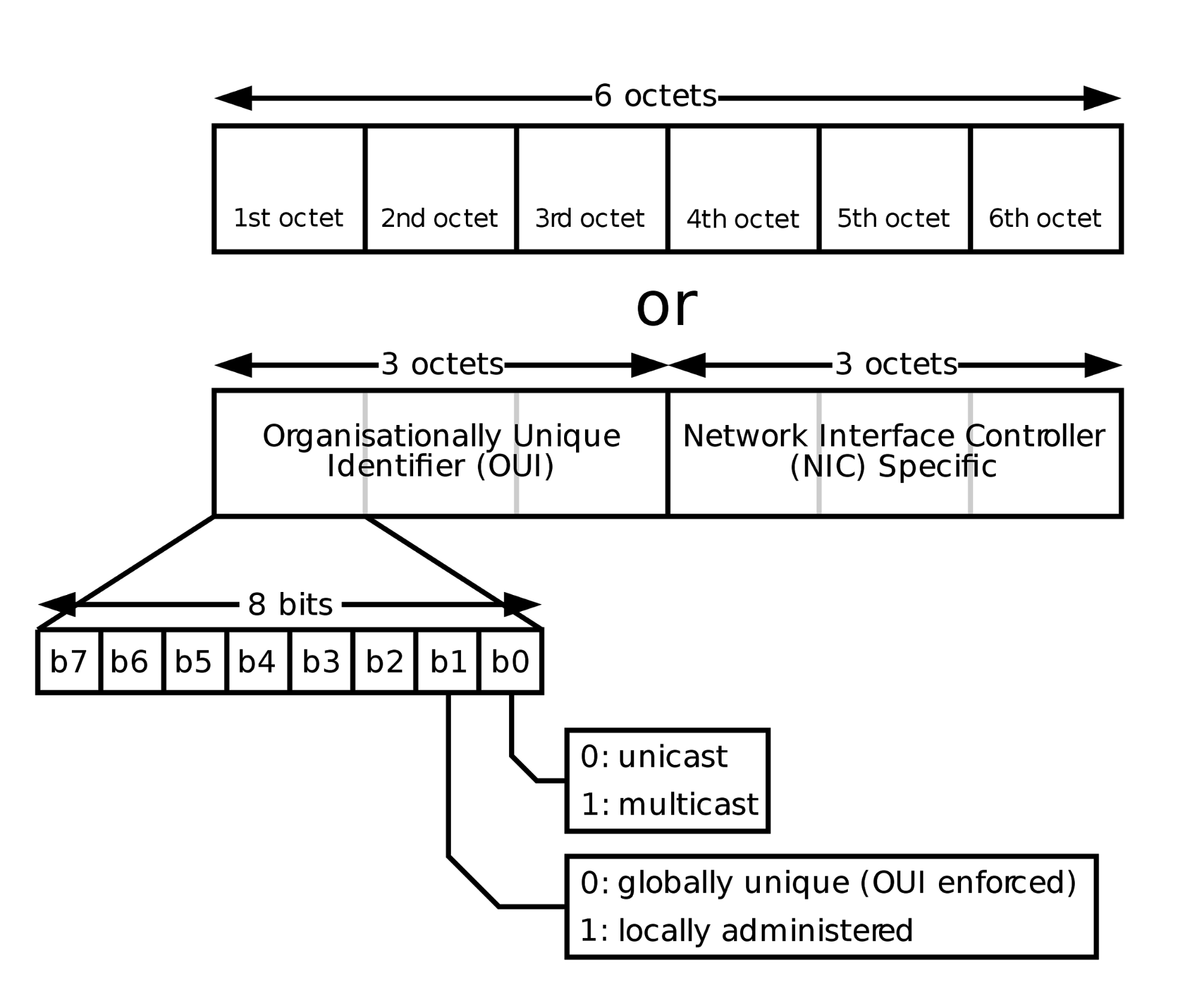
Project Zero: An iOS zero-click radio proximity exploit odyssey

Mastering Reverse Engineering

CONFidence 2015: DTrace + OSX = Fun - Andrzej Dyjak
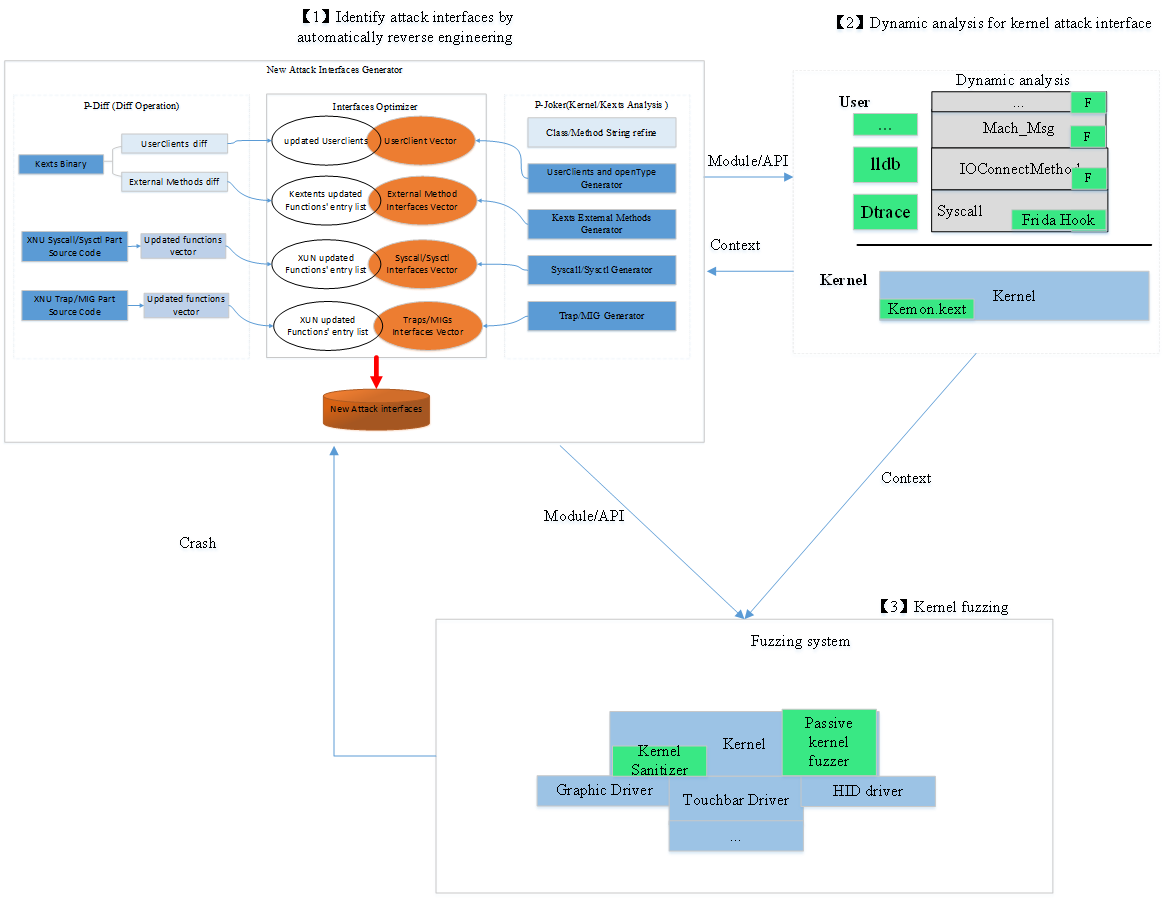
Virus Bulletin :: VB2019 paper: Play fuzzing machine – hunting iOS/macOS kernel vulnerabilities automatically and smartly

CONFidence 2015: DTrace + OSX = Fun - Andrzej Dyjak
Recomendado para você
-
Blox Fruits03 janeiro 2025
-
RBX Gum, PDF, World Wide Web03 janeiro 2025
-
 Nuevo promocode RBX.GUM 26 de Mayo #shorts03 janeiro 2025
Nuevo promocode RBX.GUM 26 de Mayo #shorts03 janeiro 2025 -
como ver los codigos de rbx gum en discord|Búsqueda de TikTok03 janeiro 2025
-
 XanderRXン03 janeiro 2025
XanderRXン03 janeiro 2025 -
Cheeks Joy Blush Face Roblox Item - Rolimon's03 janeiro 2025
-
 Cryptocurrency Prices & Marketcap – The Daily Hodl03 janeiro 2025
Cryptocurrency Prices & Marketcap – The Daily Hodl03 janeiro 2025 -
easy rbx|TikTok Search03 janeiro 2025
-
Cyan Spider Valkyrie Crown Embeds's Code & Price - RblxTrade03 janeiro 2025
-
 Seed Junky Home03 janeiro 2025
Seed Junky Home03 janeiro 2025
você pode gostar
-
 3 New Redemption Codes from 4.1 Special Program03 janeiro 2025
3 New Redemption Codes from 4.1 Special Program03 janeiro 2025 -
 Doc: Vorny Pokedex Entry Masterlist by makar-ro -- Fur Affinity03 janeiro 2025
Doc: Vorny Pokedex Entry Masterlist by makar-ro -- Fur Affinity03 janeiro 2025 -
/cdn.vox-cdn.com/uploads/chorus_image/image/57162309/DMK88JWUMAEo20j.0.png) The Daily Hilario: Guide to running Championship Manager 01-02 on03 janeiro 2025
The Daily Hilario: Guide to running Championship Manager 01-02 on03 janeiro 2025 -
 Anime Emotes Demon Fighter Emote Manga Cartoon Cute Emotes03 janeiro 2025
Anime Emotes Demon Fighter Emote Manga Cartoon Cute Emotes03 janeiro 2025 -
 Recomendação, Hitori no Shita-The Outcast03 janeiro 2025
Recomendação, Hitori no Shita-The Outcast03 janeiro 2025 -
 EDUCAÇÃO INFANTIL: dica de atividades de Informática03 janeiro 2025
EDUCAÇÃO INFANTIL: dica de atividades de Informática03 janeiro 2025 -
 You Broke My Heart - Sad Anime Girl Art Board Print for Sale by LEVANKOV Items03 janeiro 2025
You Broke My Heart - Sad Anime Girl Art Board Print for Sale by LEVANKOV Items03 janeiro 2025 -
 Scarlett Johansson Settles 'Black Widow' Lawsuit With Disney03 janeiro 2025
Scarlett Johansson Settles 'Black Widow' Lawsuit With Disney03 janeiro 2025 -
 Hope this is what you desire 🔥 — Available animatronics for rental03 janeiro 2025
Hope this is what you desire 🔥 — Available animatronics for rental03 janeiro 2025 -
 Dragon Ball: Episode of Bardock (Film) ~ All Region ~ Brand New & Factory Seal ~03 janeiro 2025
Dragon Ball: Episode of Bardock (Film) ~ All Region ~ Brand New & Factory Seal ~03 janeiro 2025



