Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 10 novembro 2024
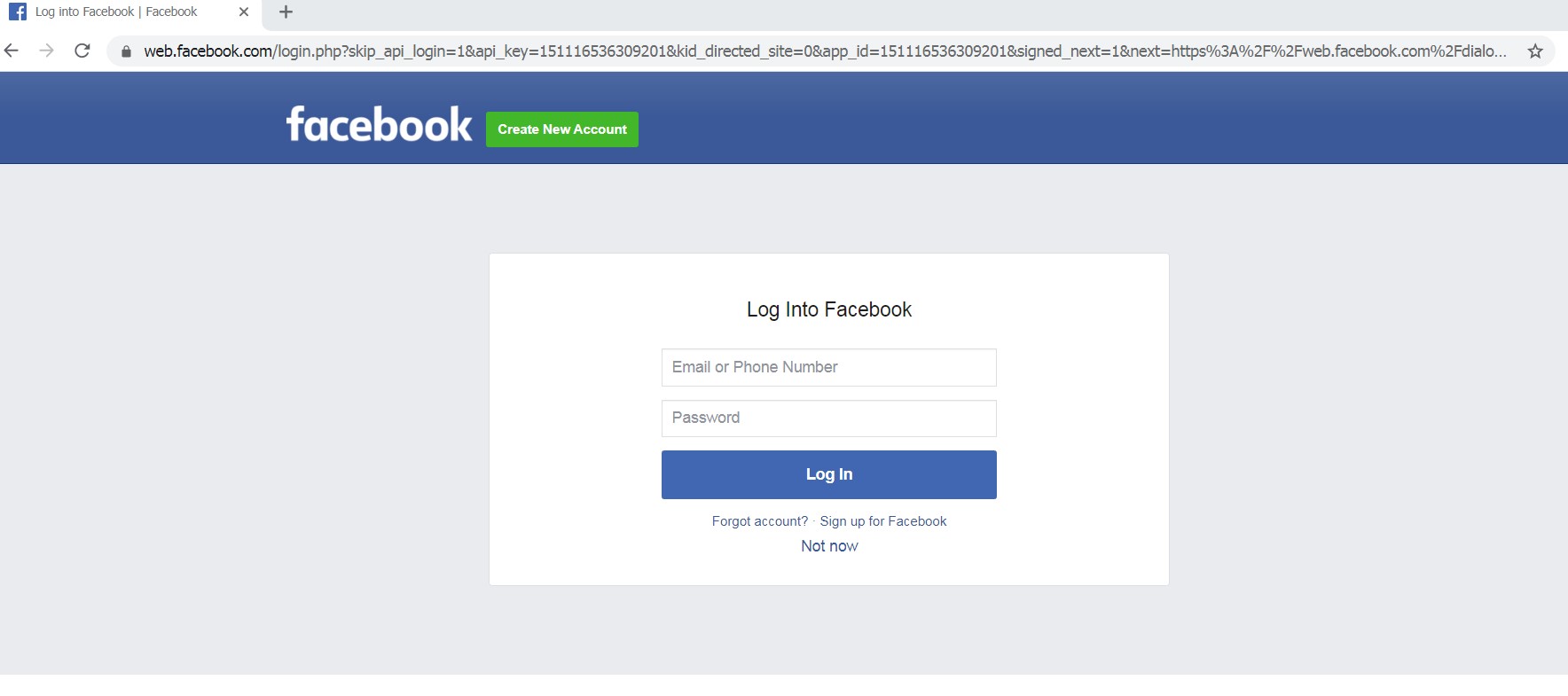
Scam Page error from Trend Micro Security
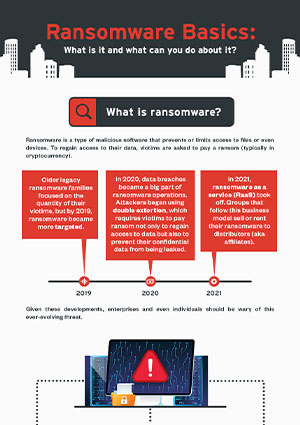
Ransomware - Definition
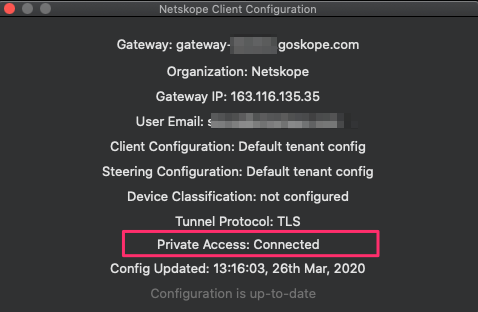
General Troubleshooting Methods - Netskope Knowledge Portal
Frontiers Block chain technology for digital financial inclusion in the industry 4.0, towards sustainable development?
Set up Authentication Agent Self-Signed Certificate with SAN - TMWS
Passed a potential security risk' in Virus/Malware Logs
Frontiers Implementation and Transfer of Predictive Analytics for Smart Maintenance: A Case Study
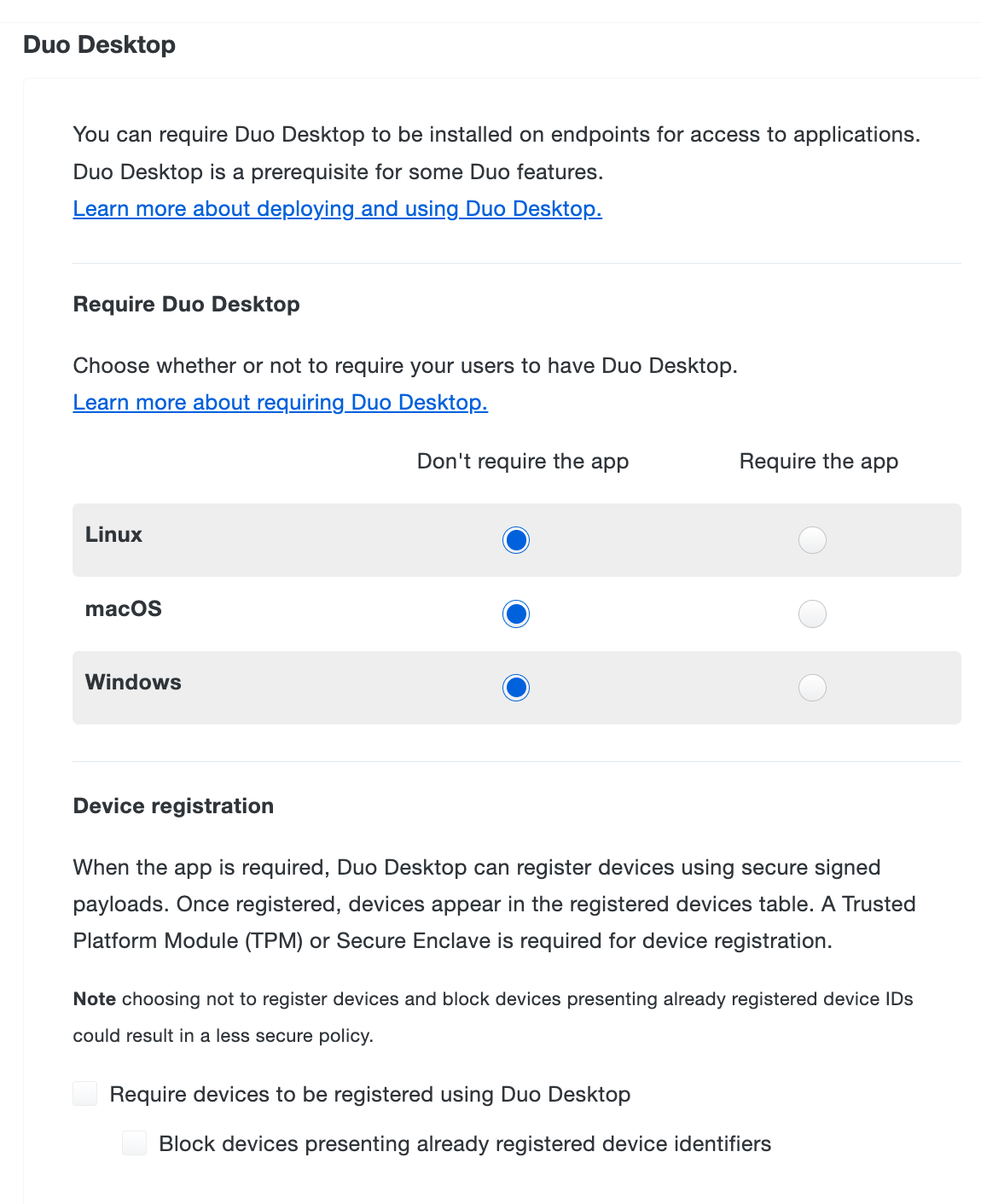
Duo Administration - Policy & Control
Empty list for endpoint and domain nodes after agent deployment - OfficeScan

Trend Micro Antivirus+ Security Review

Connected Philanthropy Podcast - Foundant Technologies
RCE (Remote Code Execution): Exploitations and Security Tips
How to generate various logs in Trend Micro for Windows
Debug log collection tool for customers - Deep Security
Recomendado para você
-
 Facebook Login UI Clone10 novembro 2024
Facebook Login UI Clone10 novembro 2024 -
 Configure Facebook Login on Your Website & Mobile App in 202010 novembro 2024
Configure Facebook Login on Your Website & Mobile App in 202010 novembro 2024 -
 Facebook Screenshot, screenshot of facebook login page on m…, Neeraj Kumar10 novembro 2024
Facebook Screenshot, screenshot of facebook login page on m…, Neeraj Kumar10 novembro 2024 -
 New Facebook Login Page10 novembro 2024
New Facebook Login Page10 novembro 2024 -
 1 Facebook login screen at system launch. Source: Screenshot from10 novembro 2024
1 Facebook login screen at system launch. Source: Screenshot from10 novembro 2024 -
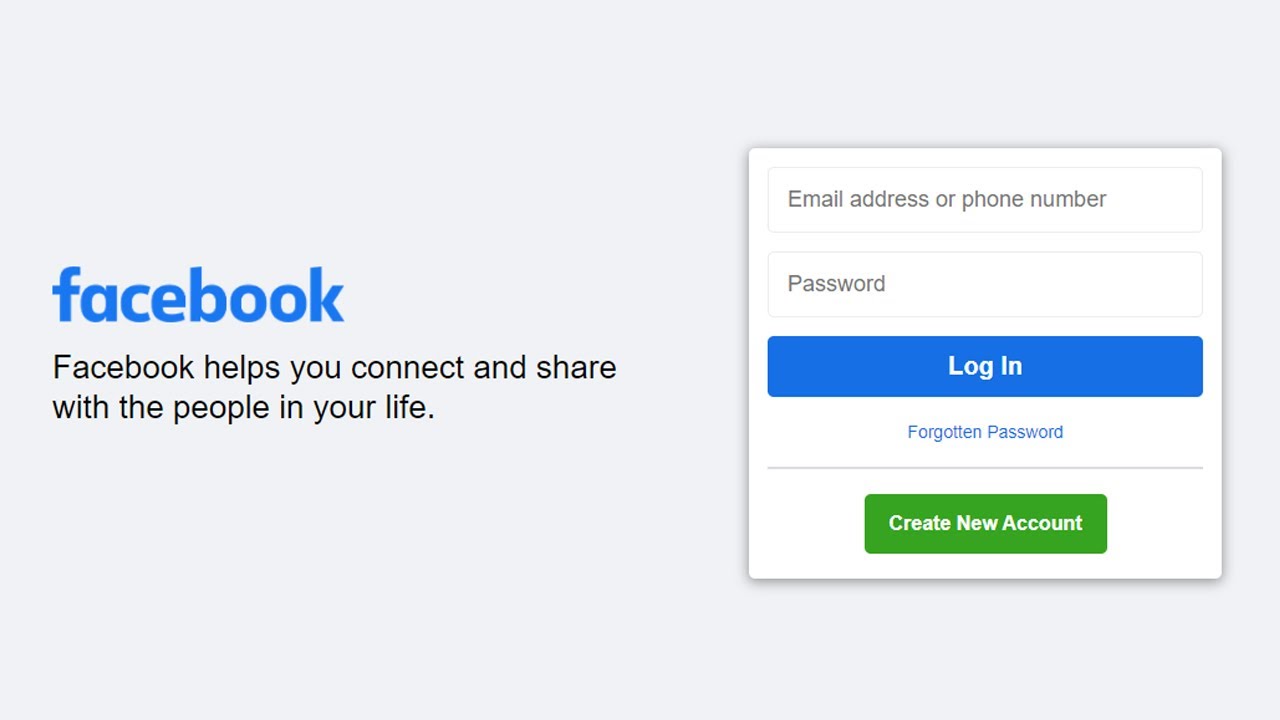 How To Create Facebook Login Page Design Using Only HTML And CSS10 novembro 2024
How To Create Facebook Login Page Design Using Only HTML And CSS10 novembro 2024 -
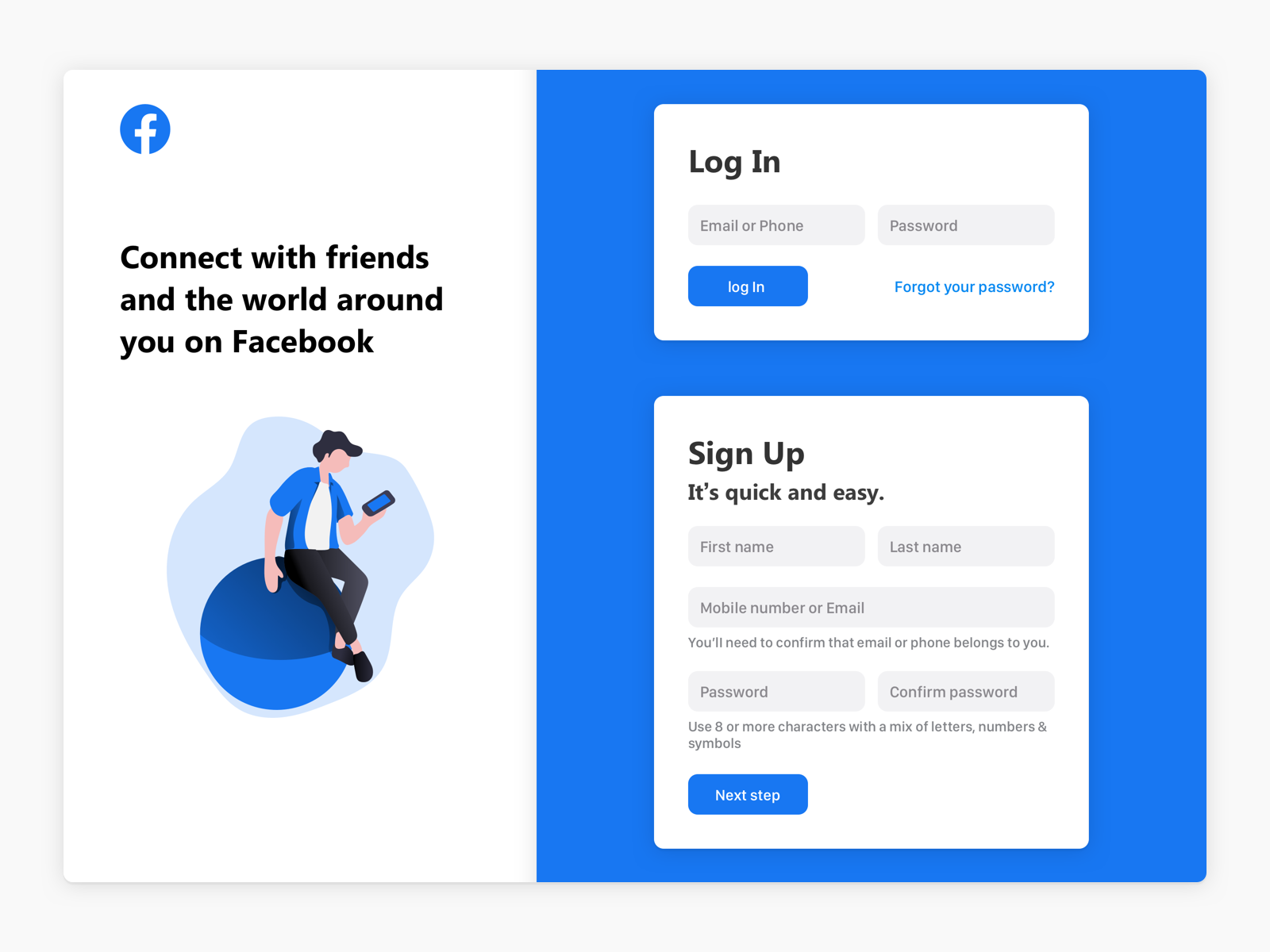 Facebook Login Screen by Dennis Bondarenko on Dribbble10 novembro 2024
Facebook Login Screen by Dennis Bondarenko on Dribbble10 novembro 2024 -
 Facebook Login Page Design by Ifeoluwa Oyelakin on Dribbble10 novembro 2024
Facebook Login Page Design by Ifeoluwa Oyelakin on Dribbble10 novembro 2024 -
 SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook10 novembro 2024
SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook10 novembro 2024 -
 Facebook opens Ads Page instead of regular homepage after login10 novembro 2024
Facebook opens Ads Page instead of regular homepage after login10 novembro 2024
você pode gostar
-
 English Chess Opening –10 novembro 2024
English Chess Opening –10 novembro 2024 -
 Top 100 League of Legends Wallpapers For Wallpaper Engine 202210 novembro 2024
Top 100 League of Legends Wallpapers For Wallpaper Engine 202210 novembro 2024 -
 Curso da Abertura Italiana - MN Gérson Peres10 novembro 2024
Curso da Abertura Italiana - MN Gérson Peres10 novembro 2024 -
 Smart Cars: Reviews, Pricing, and Specs10 novembro 2024
Smart Cars: Reviews, Pricing, and Specs10 novembro 2024 -
Crunchyroll.pt - Irmãos! 👊🔥 (JUJUTSU KAISEN)10 novembro 2024
-
 Blindfolded man10 novembro 2024
Blindfolded man10 novembro 2024 -
 Oklahoma State University10 novembro 2024
Oklahoma State University10 novembro 2024 -
 Copa do Mundo Feminina inicia mata-mata no fim de semana10 novembro 2024
Copa do Mundo Feminina inicia mata-mata no fim de semana10 novembro 2024 -
 Plantel do City vale o dobro do Inter Milão e há um gigante que faz toda a diferença10 novembro 2024
Plantel do City vale o dobro do Inter Milão e há um gigante que faz toda a diferença10 novembro 2024 -
14+ Jogos de Xbox 360 de Todas As Categorias10 novembro 2024

