LetsDefend on X: Top 100 Reused Passwords / X
Por um escritor misterioso
Last updated 23 dezembro 2024


Malware Threats. Today, computers and other digital…, by Enes Adışen
Email Analysis Challenge-LetsDefend Lab Walkthrough, by Joseph Karuga

OWASP Top 10, TryHackMe Writeup. This document delves into the OWASP Top…, by Lixin Zhang, Oct, 2023
GitHub - LetsDefend/SOC-Interview-Questions: SOC Interview Questions
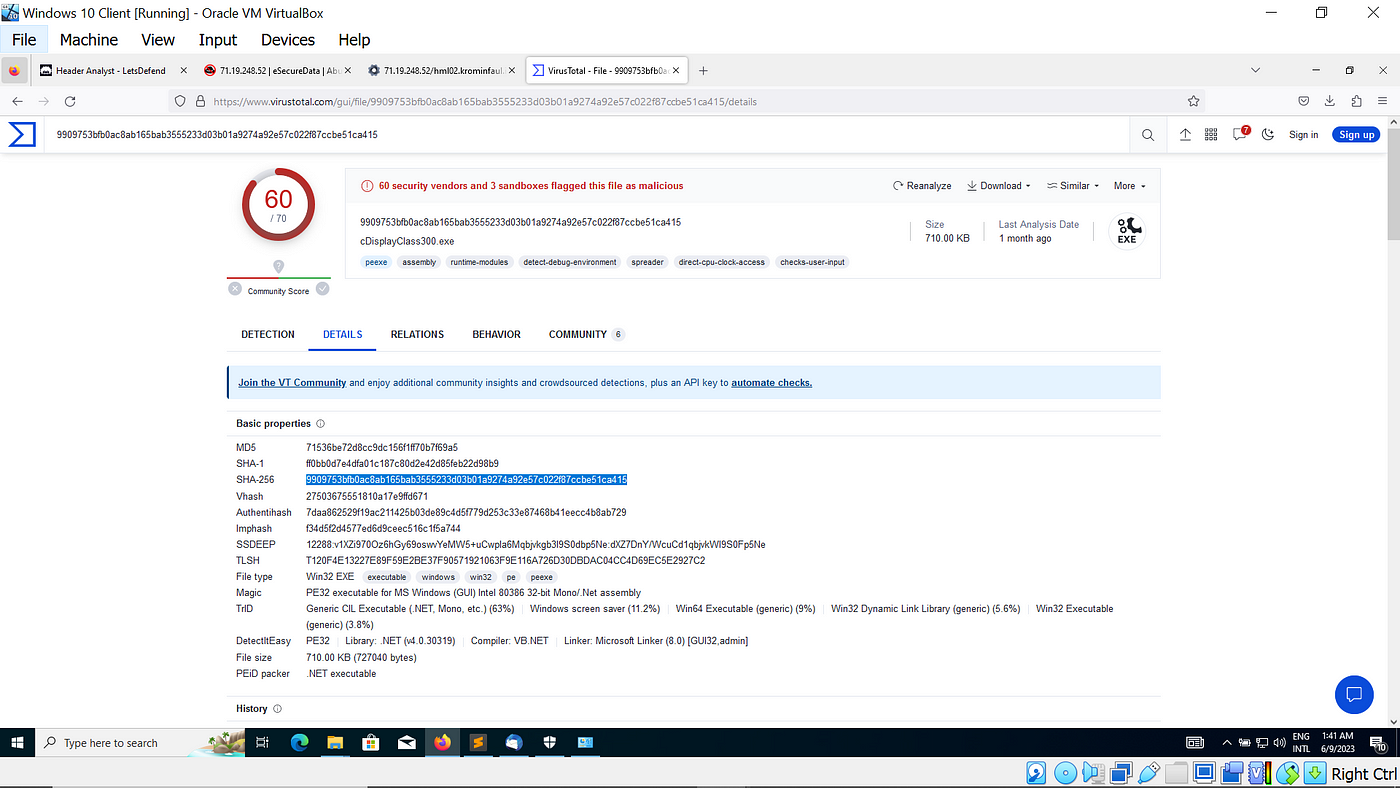
ctf/solutions/letsdefend_icedID_malware_family.md at main · 1d8/ctf · GitHub

Cyber Security Interview Q&A - DETECTX

Naiden Nedelchev on LinkedIn: What might be easily expected when the outcome of a(ny) controlling…

Knock Knock : Hack the box Sherlock, by CyberJunnkie, Dec, 2023

Richard Jones on LinkedIn: #linuxterminal #octalascii #terminalhacks #linuxcommands #tips #learning…
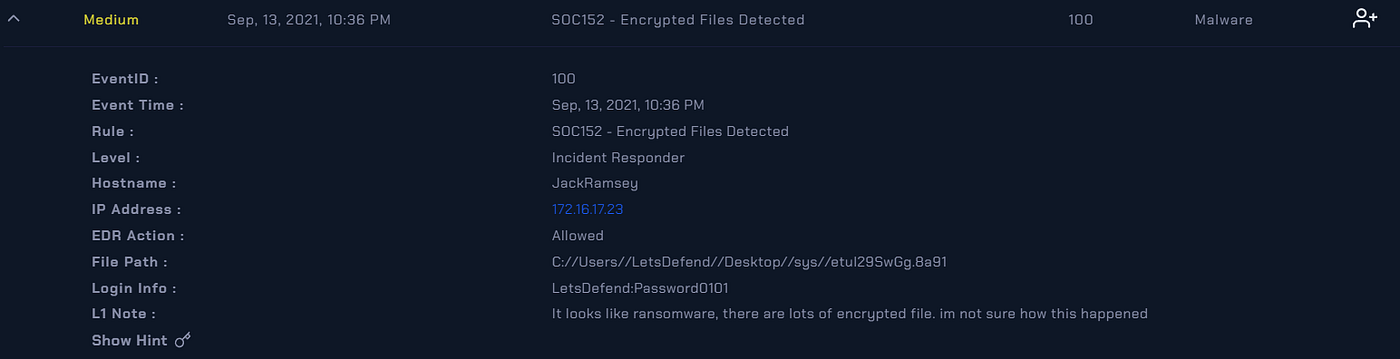
LetsDefend:IR — SOC152 — EVENT ID 100, by AliD

How Adversaries Can Persist with AWS User Federation

Kapeed

Harun Seker, CISSP on LinkedIn: #password #cybersecurity
LetsDefend: Dynamic Malware Analysis Part 1, by Cybertech Maven

S. Rohit on LinkedIn: #bugbounty #bugbountytips #bugbountytip #cybersecurity #ethicalhacking…
Recomendado para você
-
 How to share Google Drive files to a chat23 dezembro 2024
How to share Google Drive files to a chat23 dezembro 2024 -
 How to Upload Video to Google Drive EASILY - BizCrown Media Digital Marketing23 dezembro 2024
How to Upload Video to Google Drive EASILY - BizCrown Media Digital Marketing23 dezembro 2024 -
 Google search bar displays up and down arrow in box next to search : r/techsupport23 dezembro 2024
Google search bar displays up and down arrow in box next to search : r/techsupport23 dezembro 2024 -
GitHub - eliraneliassy/angular-google-maps-poc23 dezembro 2024
-
 Google'da Anlık Neler Aranıyor? Google'dan Yeni Bir Uygulama23 dezembro 2024
Google'da Anlık Neler Aranıyor? Google'dan Yeni Bir Uygulama23 dezembro 2024 -
 Learn how to setup Google Data Studio report tracking in Google Analytics23 dezembro 2024
Learn how to setup Google Data Studio report tracking in Google Analytics23 dezembro 2024 -
Solved: In RTE I want to add some html tag - Adobe Experience League Community - 56871423 dezembro 2024
-
 Facing Problem with CloudSQL - Terraform Resource Block - Google - HashiCorp Discuss23 dezembro 2024
Facing Problem with CloudSQL - Terraform Resource Block - Google - HashiCorp Discuss23 dezembro 2024 -
 Alyxbrian Observable23 dezembro 2024
Alyxbrian Observable23 dezembro 2024 -
 c# - Issue : Cut off the description when Add event to google calendar from .ics file - Stack Overflow23 dezembro 2024
c# - Issue : Cut off the description when Add event to google calendar from .ics file - Stack Overflow23 dezembro 2024
você pode gostar
-
 GamePigeon for Android - javatpoint23 dezembro 2024
GamePigeon for Android - javatpoint23 dezembro 2024 -
 Authentic Nintendo DS Games for DS / Dslite / Dsi / 3DS XL and - Israel23 dezembro 2024
Authentic Nintendo DS Games for DS / Dslite / Dsi / 3DS XL and - Israel23 dezembro 2024 -
 Gray alien Desenho de desenho animado, garota alienígena, mamífero, mão, manga png23 dezembro 2024
Gray alien Desenho de desenho animado, garota alienígena, mamífero, mão, manga png23 dezembro 2024 -
 Uncharted 3: Drakes Deception p/ PS3 - Sony - Jogos de Aventura - Magazine Luiza23 dezembro 2024
Uncharted 3: Drakes Deception p/ PS3 - Sony - Jogos de Aventura - Magazine Luiza23 dezembro 2024 -
 Secret Words - A mod that creates 5 custom planets on Outer Wilds23 dezembro 2024
Secret Words - A mod that creates 5 custom planets on Outer Wilds23 dezembro 2024 -
 Bloodborne PSX developer is making Bloodborne Kart next23 dezembro 2024
Bloodborne PSX developer is making Bloodborne Kart next23 dezembro 2024 -
 Xbox One Seminovo - BeB Games23 dezembro 2024
Xbox One Seminovo - BeB Games23 dezembro 2024 -
Joelle 🩵 on X: Classroom of the elite season 2 BD volume 2 improvements #you_zitsu #よう実 / X23 dezembro 2024
-
 Pokeball Logo Png Download - Pokeball Png Full Size Png Emoji23 dezembro 2024
Pokeball Logo Png Download - Pokeball Png Full Size Png Emoji23 dezembro 2024 -
 Killing Stalking Cosplay Badge Yoonbum Brooch Pin Anime Accessories For Clothes Backpack Decoration gift23 dezembro 2024
Killing Stalking Cosplay Badge Yoonbum Brooch Pin Anime Accessories For Clothes Backpack Decoration gift23 dezembro 2024